Disable Mandatory Windows Hello for Business Prompt on Azure AD joined Devices
If you join your device to Azure AD by using the Access work or school settings, the device by default will be automatically registered with Windows Hello for Business support aka Windows Hello for Business provisioning.
Windows Hello for Business provisioning begins immediately after the user has signed in, after the user profile is loaded, but before the user receives their desktop. Windows only launches the provisioning experience if all the prerequisite checks pass. You can determine the status of the prerequisite checks by viewing the User Device Registration in the Event Viewer under Applications and Services Logs\Microsoft\Windows.
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-deployment-guide#provisioning
- Join a Windows 10 device to Azure AD
- Adding further User's from your Azure AD to the device
- Disable Windows Hello for Business by using a Group Policy
- Disable Windows Hello for Business by using Microsoft Intune
- Windows Hello vs. Windows Hello for Business
- Determine if Windows Hello for Business is used for your Windows Sign In
- Links
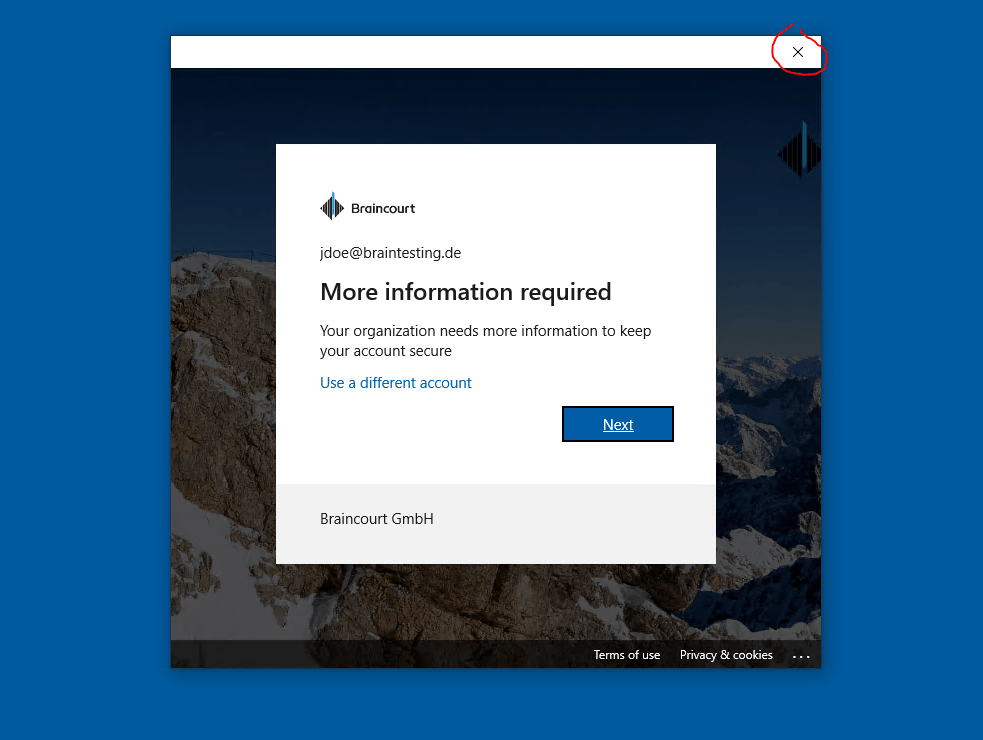
Then you will be prompted during the first login with your Azure AD (Office 365) account to set up Windows Hello for Business as follows.
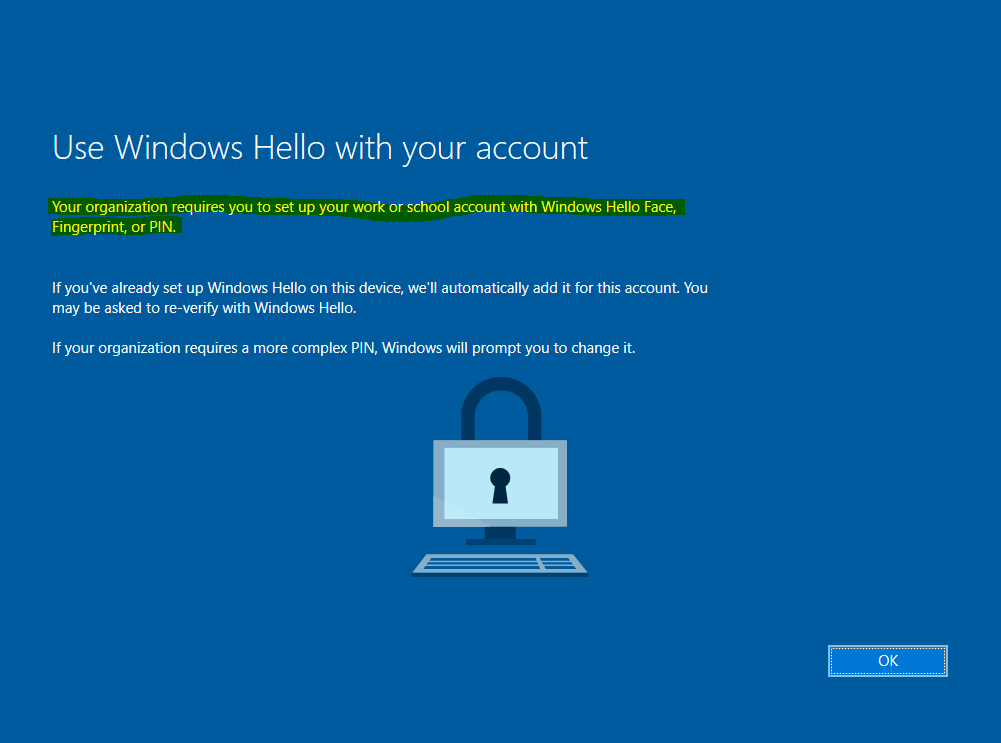
In this post we will see, how to disable Windows Hello for Business for whatever reason. Generally I would not recommend to disable it, as it can intensely reduce the risk of keyloggers, password phishing or password interception in general, but in some cases it can be useful to disable it.
For example multiple users want to logon to a device on rare occasions, then this behavior would be annoying to only set up Windows Hello for Business for a few times the user wants to logon. The set up and therefore the PIN will be tied only to that specific device and cannot be used from the user on other devices or its own.
For such cases, I think the best option is to still enable Windows Hello for Business by using a group policy, applied to computers (Computer configuration) with the option Do not start Windows Hello provisioning after sign-in.
By using this policy, user’s are still able to set up Windows Hello for Business on their own if wanted but won’t be prompted mandatory after sign-in to set up as in the screen above shown.
You will see further down how to enable that option.
How many users can enroll for Windows Hello for Business on a single Windows 10 computer?
The maximum number of supported enrollments on a single Windows 10 computer is 10. This lets 10 users each enroll their face and up to 10 fingerprints. While we support 10 enrollments, we will strongly encourage the use of Windows Hello security keys for the shared computer scenario when they become available.
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-faq#how-many-users-can-enroll-for-windows-hello-for-business-on-a-single-windows-10-computer
But first I will show here how you can join a windows 10 device to Azure AD.
In order to be able to join your device to Azure AD, your tenant must have enabled the option Users may join devices to Azure AD in the Azure portal under Azure Active Directory -> Devices -> Device settings as follow.
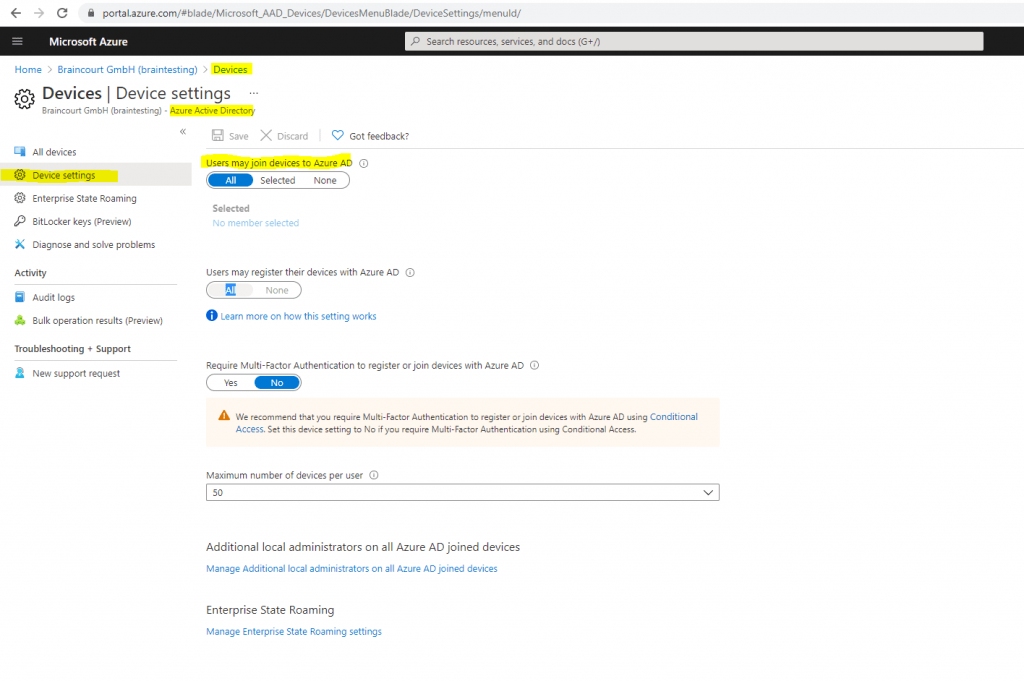
Join a Windows 10 device to Azure AD
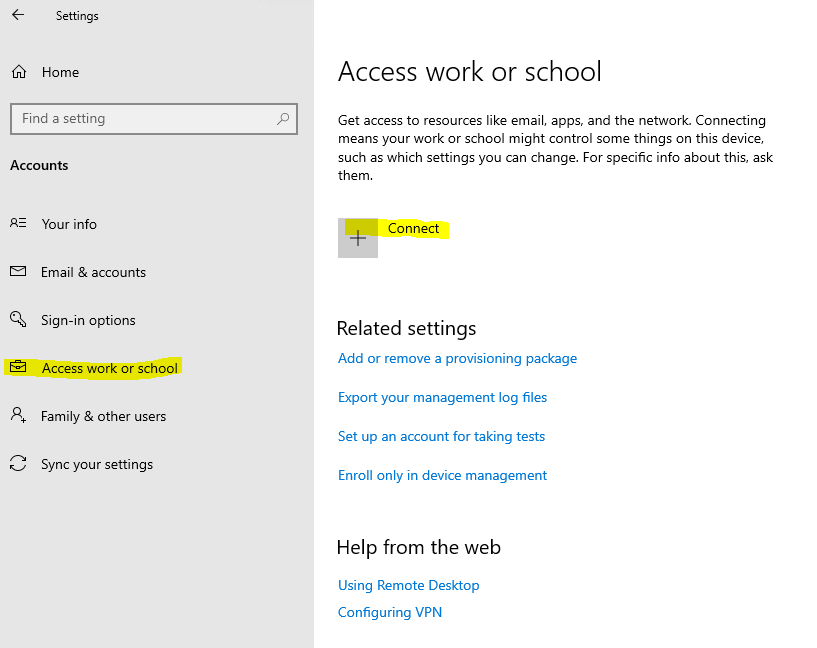
To join a windows 10 device to Azure AD you can click under Settings -> Accounts -> Access work or school on the button below.
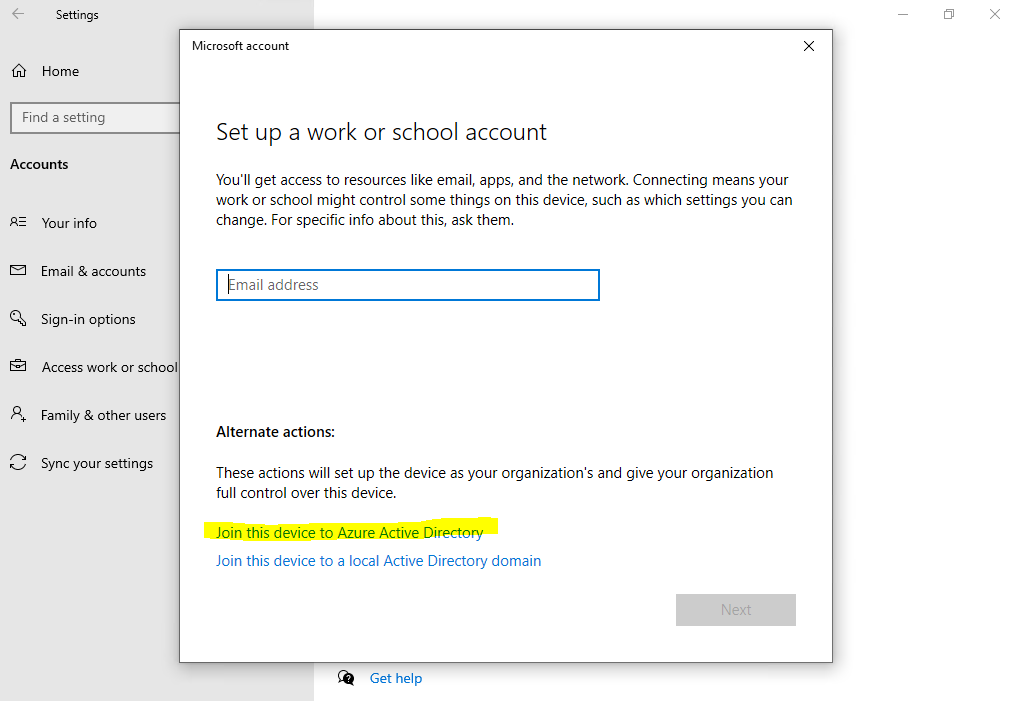
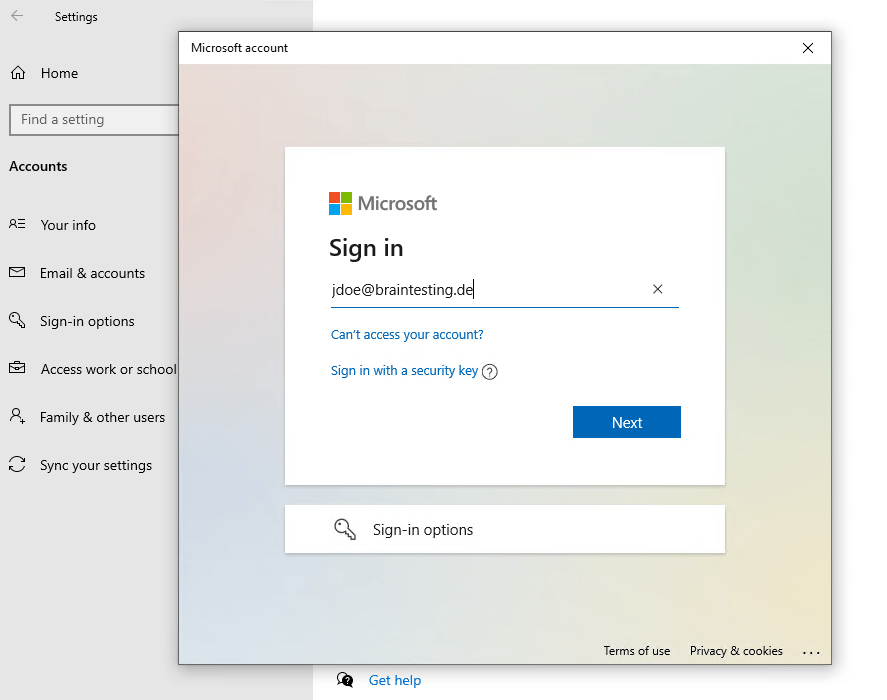
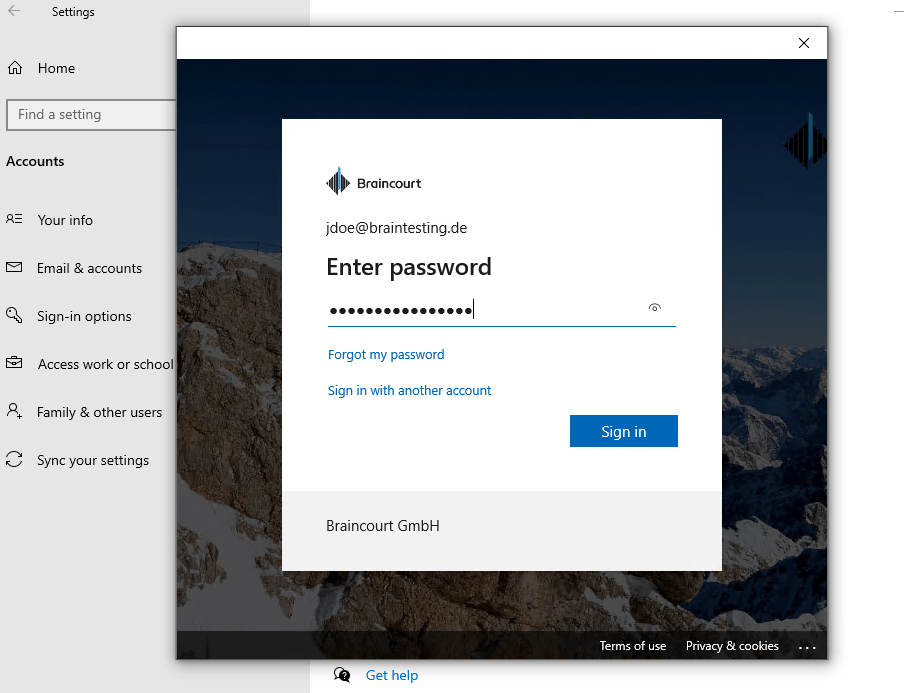
Here you need to click on Join this device to Azure Active Directory. To only register the device to Azure AD, you can enter your username and click on Next.
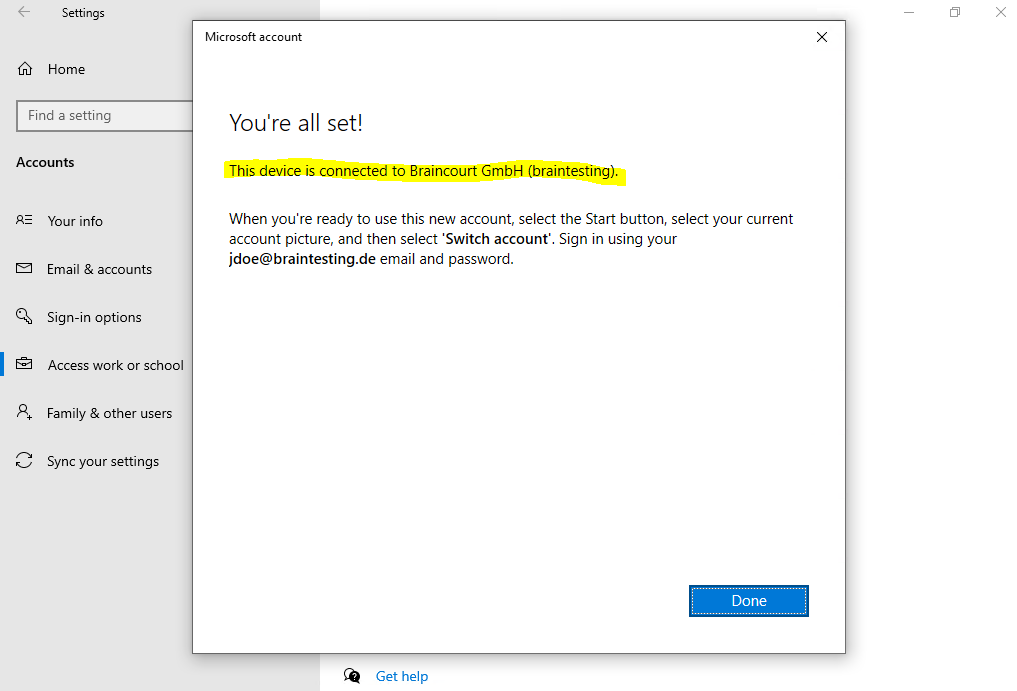
Azure AD joined devices
https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-azure-ad-join
Azure AD joined devices are signed in to using an organizational Azure AD account. Access to resources in the organization can be further limited based on that Azure AD account and Conditional Access policies applied to the device identity.
Azure AD registered devices
https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-azure-ad-register
The goal of Azure AD registered devices is to provide your users with support for the bring your own device (BYOD) or mobile device scenarios. In these scenarios, a user can access your organization’s resources using a personal device.
Hybrid Azure AD joined devices
https://docs.microsoft.com/en-us/azure/active-directory/devices/concept-azure-ad-join-hybrid
Organizations with existing Active Directory implementations can benefit from some of the functionality provided by Azure Active Directory (Azure AD) by implementing hybrid Azure AD joined devices. These devices are joined to your on-premises Active Directory and registered with Azure Active Directory.
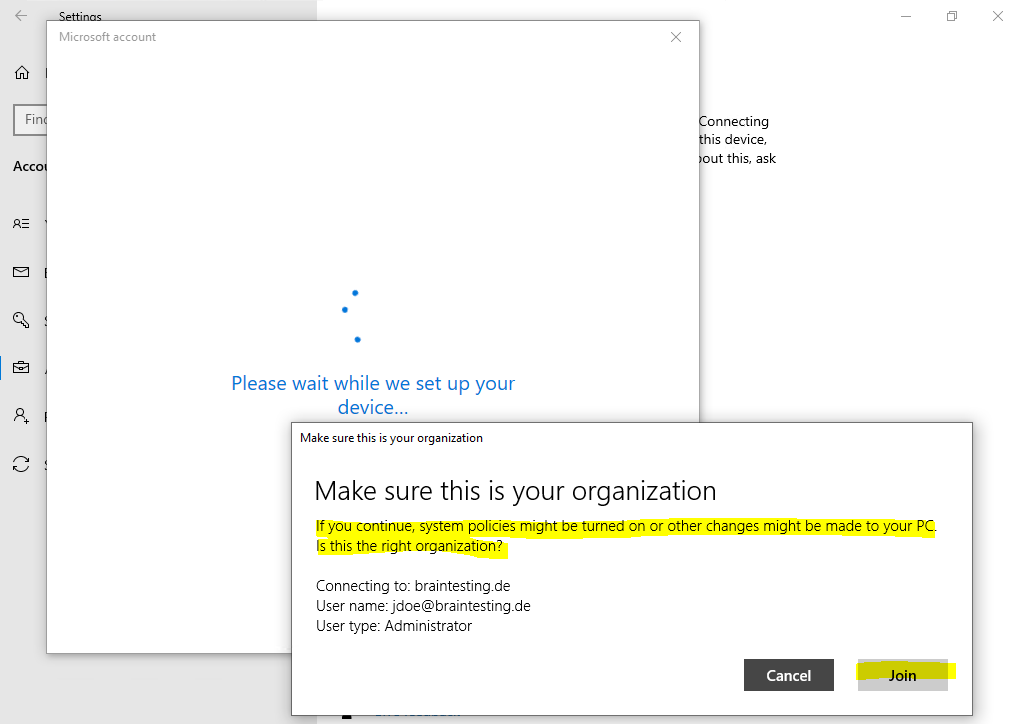
Click on Join
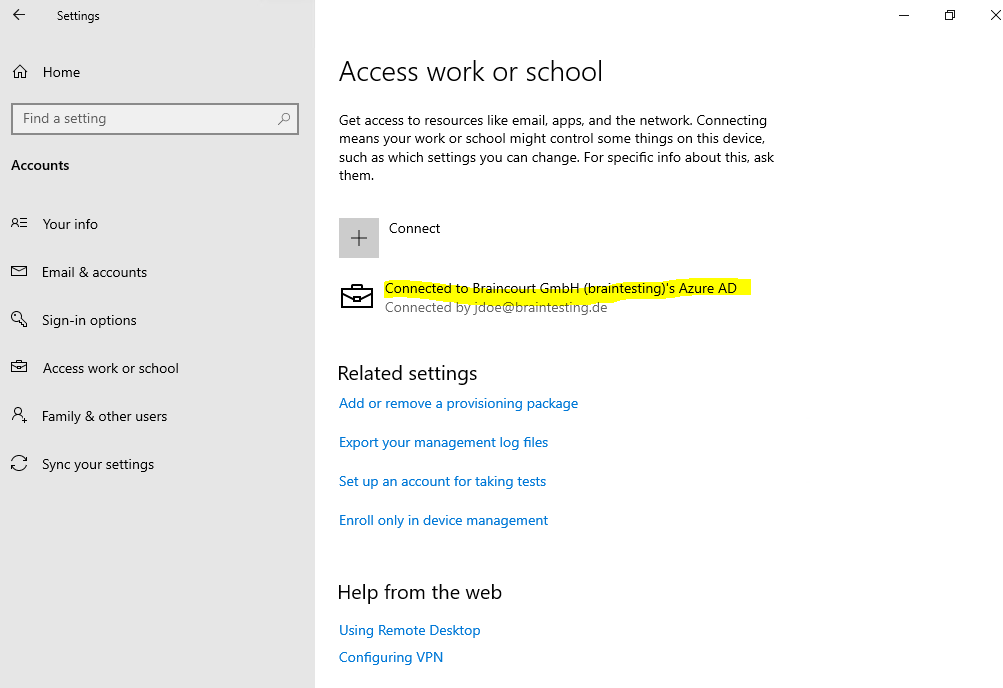
Adding further User’s from your Azure AD to the device
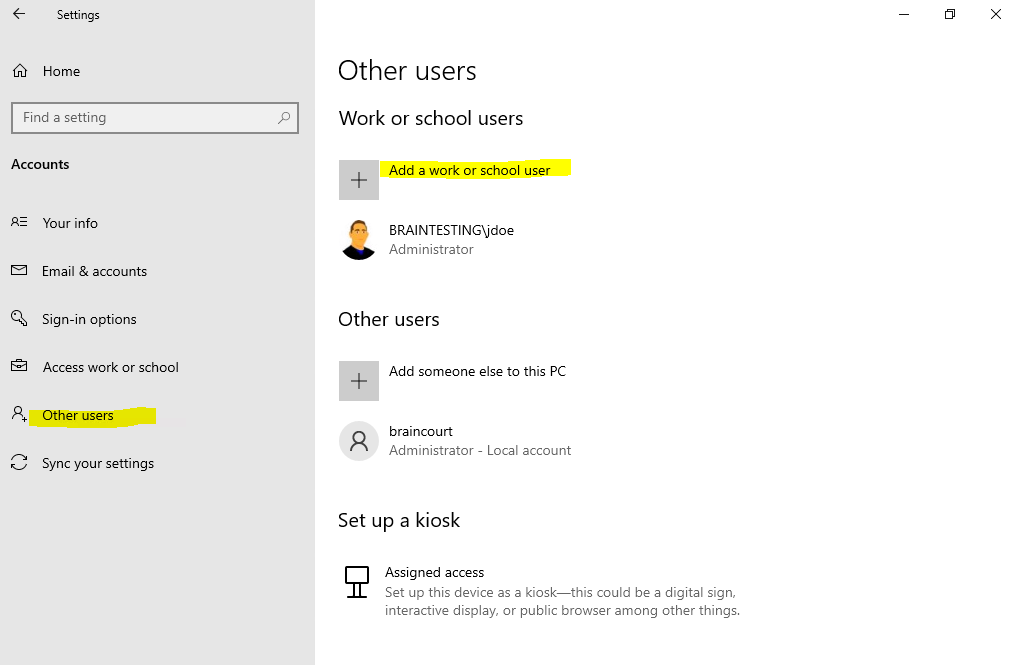
You can also add further users from your Azure AD by clicking under Settings -> Accounts -> Other users on the button Add a work or school user as below.
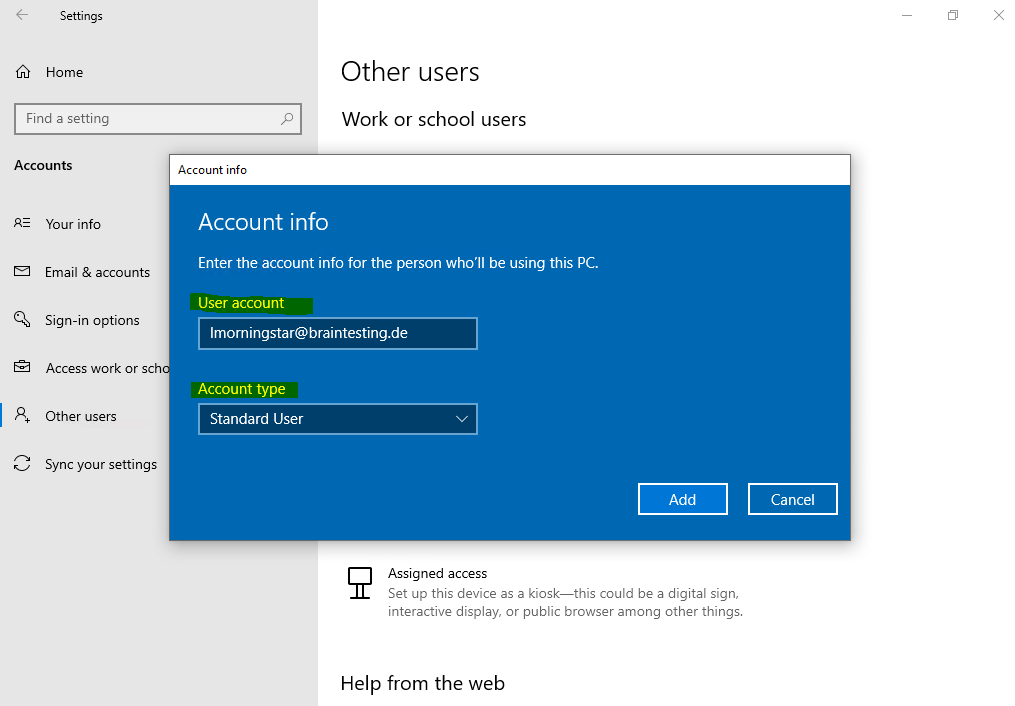
You can also choose what account type the user should be on the device, administrator or standard user.
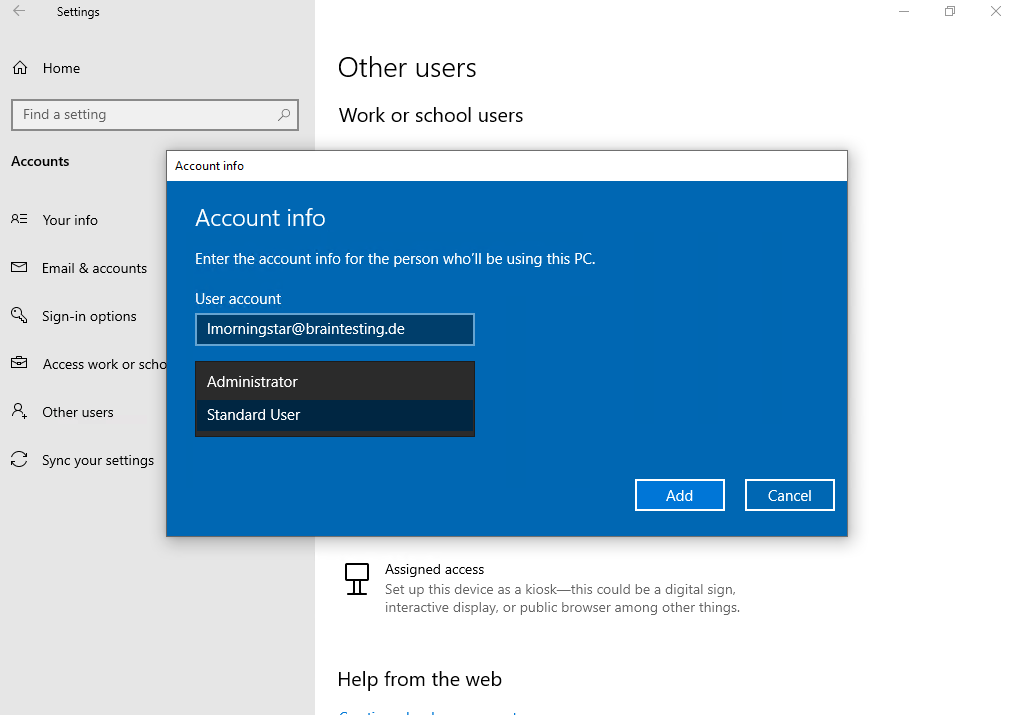
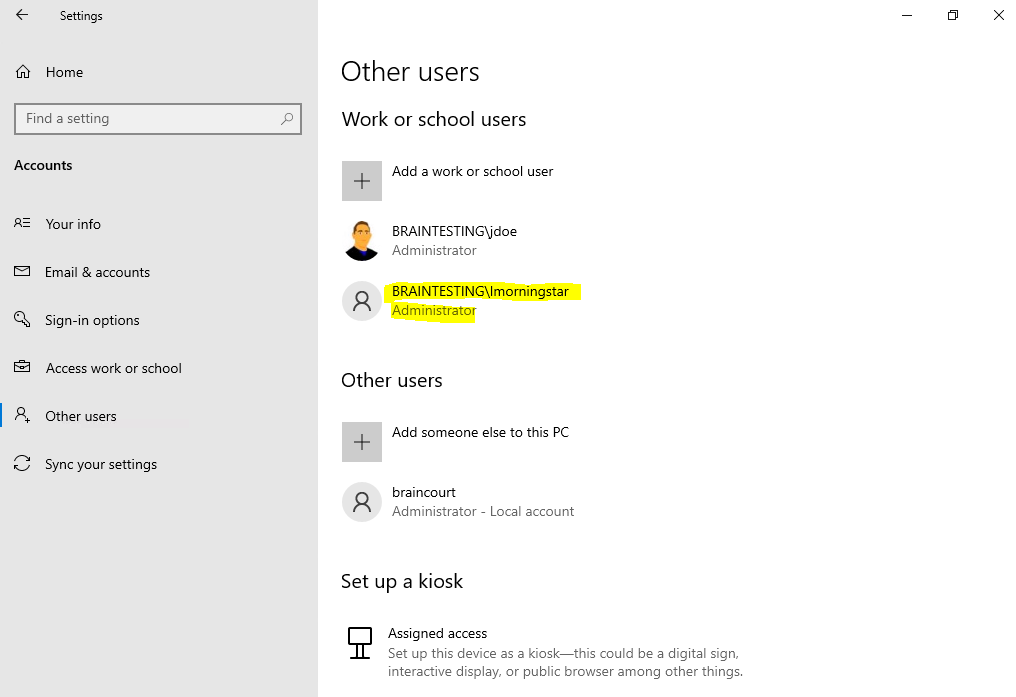
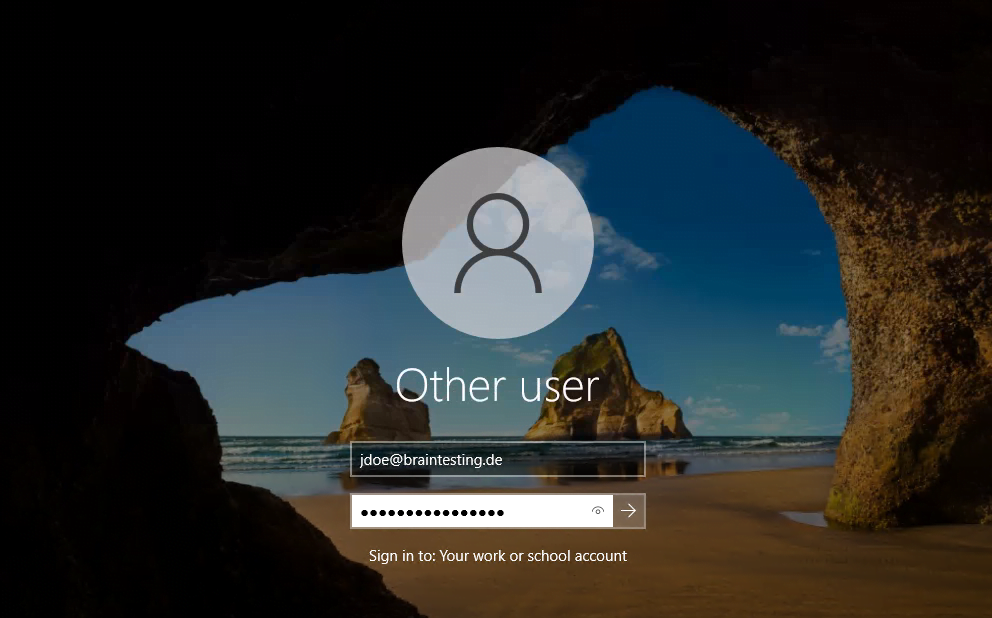
Now I can logon to the device by using my Azure AD/Office 365 account.
The user profile for this new user is created on the device
And now as seen at the beginning I will be prompted to set up Windows Hello for Business.
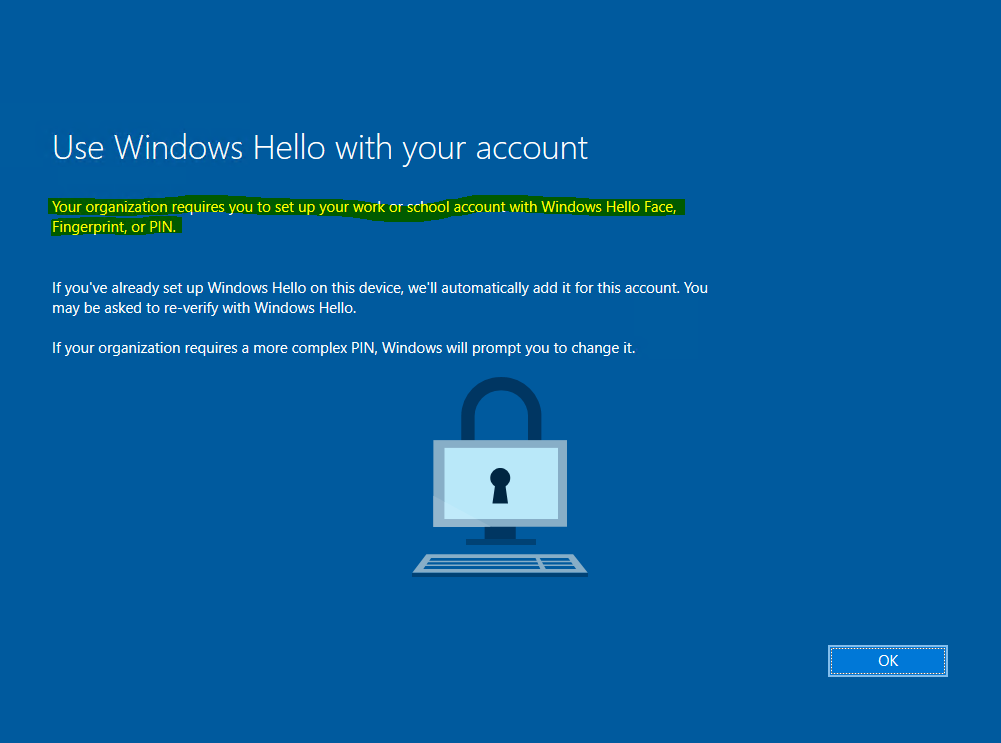
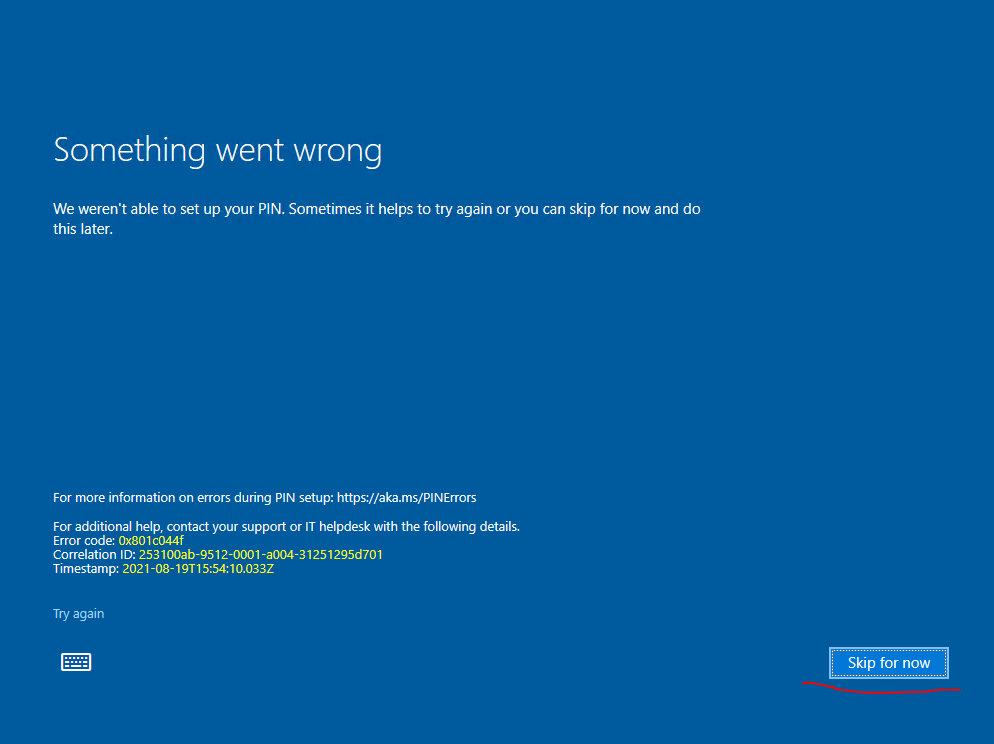
If you do not want to use Windows Hello for Business, you can click on the OK button above, after that you will be prompted with the dialog below to enter your username and password again. That dialog you have to close and click it away to be able to skip the set up of Windows Hello for Business as follows.
Now you can click on Skip for now and as it implies, unfortunately the next time you logon to your device it will appear again.
Disable Windows Hello for Business by using a Group Policy
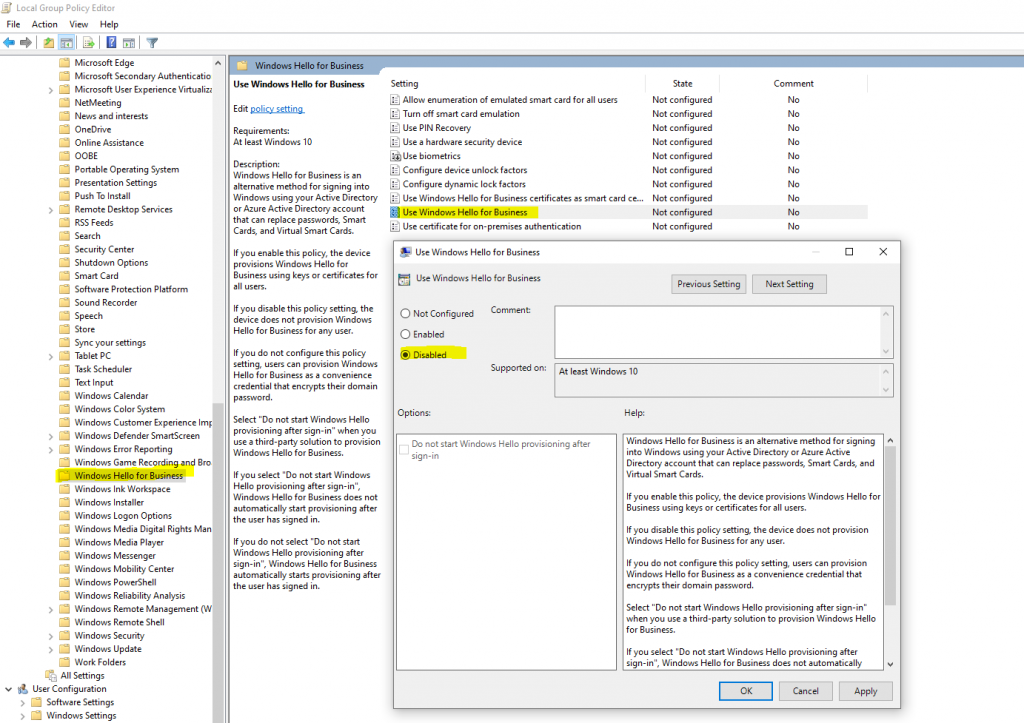
One way to disable Windows Hello for Business is by using a group policy.
Computer Configuration or User Configuration -> Administrative Templates -> Windows Components -> Windows Hello for Business
Here for Use Windows Hello for Business select Disabled.
Policy conflicts from multiple policy sources
Windows Hello for Business is designed to be managed by Group Policy or MDM but not a combination of both. If policies are set from both sources it can result in a mixed result of what is actually enforced for a user or device.
Policies for Windows Hello for Business are enforced using the following hierarchy: User Group Policy > Computer Group Policy > User MDM > Device MDM > Device Lock policy.
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization#policy-conflicts-from-multiple-policy-sources
If you disable Windows Hello for Business, no matter which way you use, GPOs or Microsoft Intune, the downside of both ways is that user’s won’t be able to add an option later by itself if they want to.
Also the user’s won’t be able to set up Windows Hello convenience PIN. The differences between Windows Hello for Business and Windows Hello (convenient sign-in) we will see further down in this post.
To only disable the Windows Hello for Business provisioning process after sign-in on the device, which prompts the dialog as shown above, you can enable Windows Hello for Business with that GPO and check the option Do not start Windows Hello provisioning after sign-in as shown below.
That option is available in both sections of the GPO, the Computer configuration and User configuration.
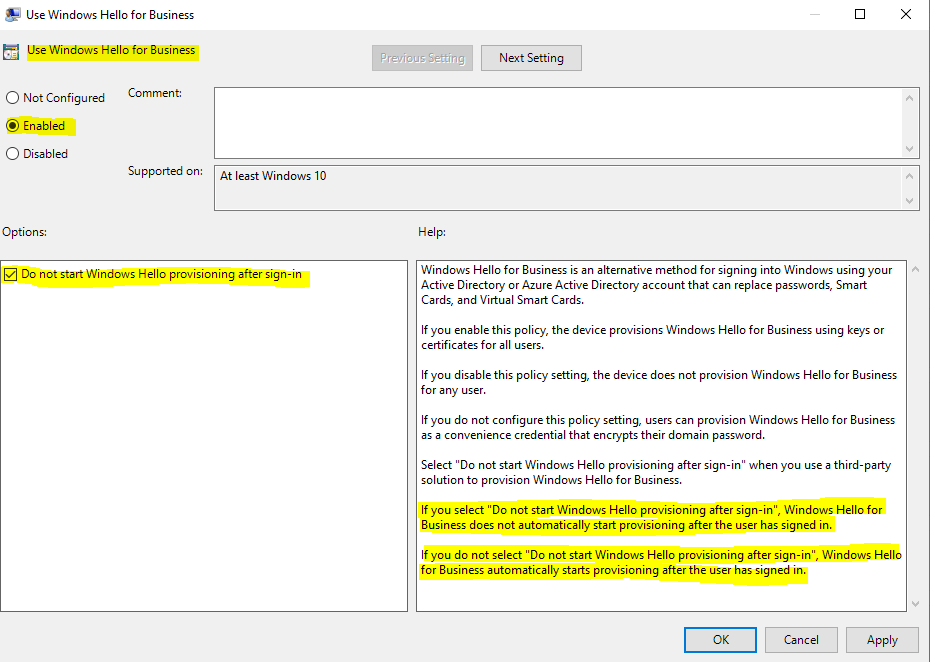
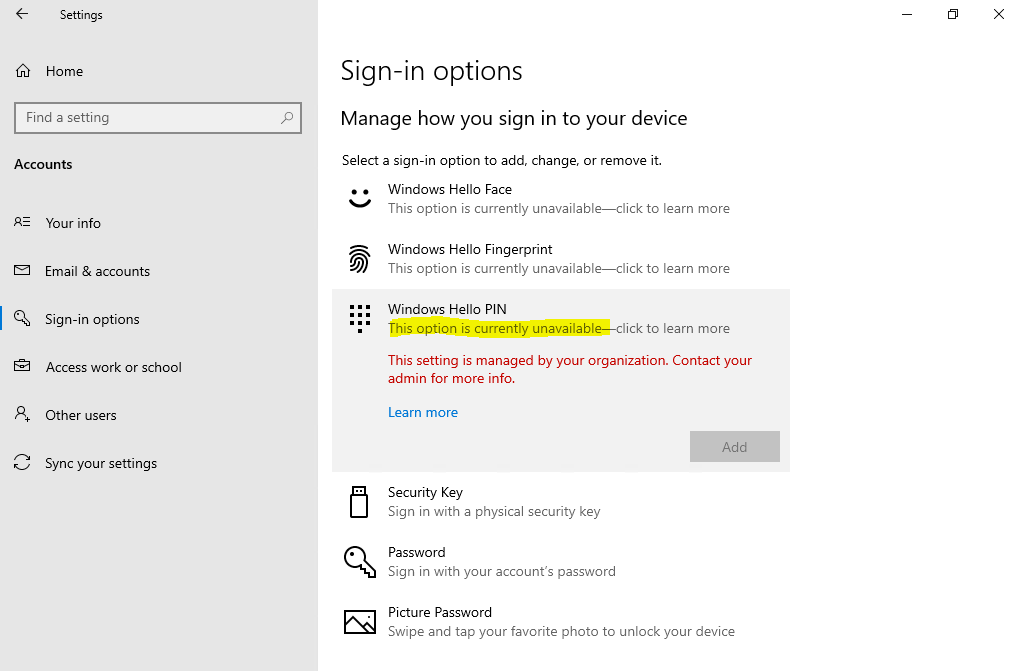
If the option above is checked, user’s won’t be prompted after sign-in to set up Windows Hello for Business as shown below.
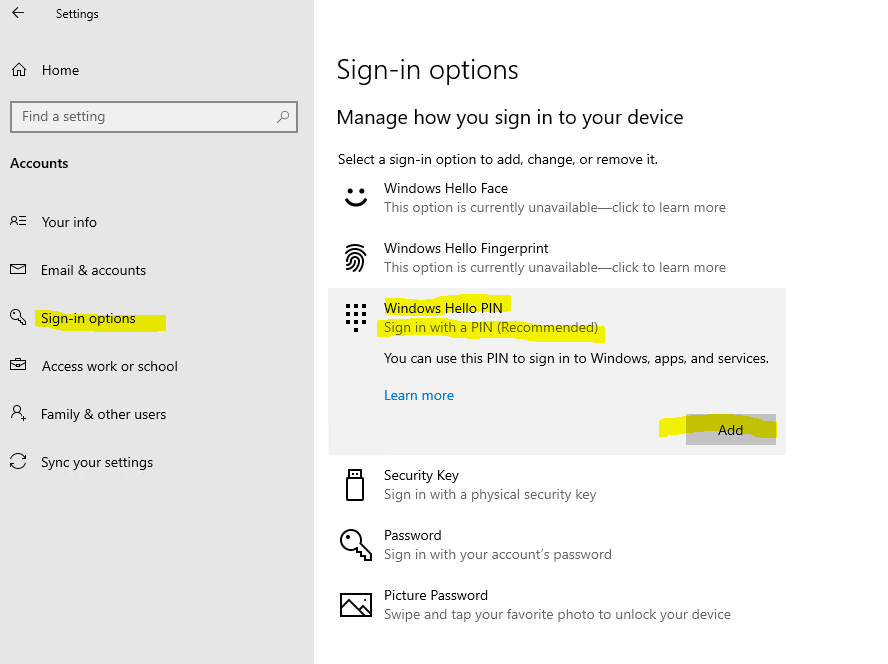
However the user’s still be able to set up Windows Hello for Business on their own under Settings -> Accounts -> Sign-in options as follows.
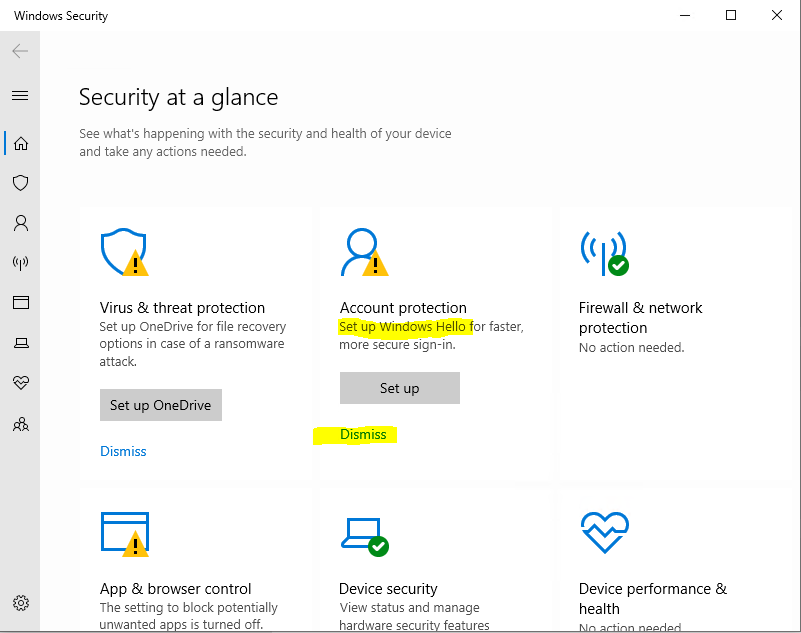
Further if not provisioned, you will see a warning in the Windows Security Center to set up Windows Hello which you can also dismiss.
Disable Windows Hello for Business by using Microsoft Intune
To disable Windows Hello for Business we can also use Microsoft Intune which we will find in the Microsoft Endpoint Manager admin center portal.
Microsoft Endpoint Manager overview
Microsoft Endpoint Manager helps deliver the modern workplace and modern management to keep your data secure, in the cloud and on-premises. Endpoint Manager includes the services and tools you use to manage and monitor mobile devices, desktop computers, virtual machines, embedded devices, and servers.
Endpoint Manager combines services you may know and already be using, including Microsoft Intune, Configuration Manager, Desktop Analytics, co-management, and Windows Autopilot. These services are part of the Microsoft 365 stack to help secure access, protect data, and respond and manage risk.
Source: https://docs.microsoft.com/en-us/mem/endpoint-manager-overview
To be able to use Microsoft Intune, you will also need a valid license which is for example included in the Enterprise Mobility + Security licenses.
Here click on Devices
Click on Windows
Click on Windows enrollment and Windows Hello for Business
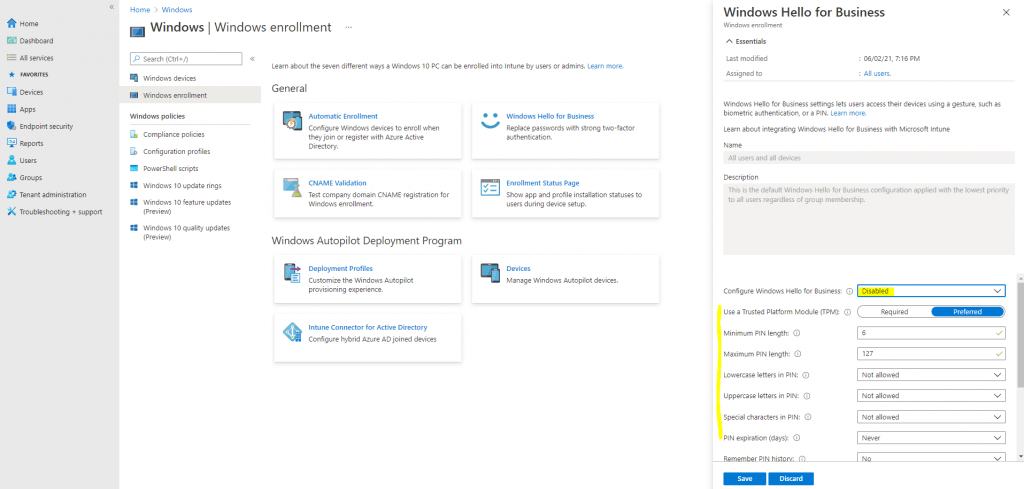
Here we can switch under Configure Windows Hello for Business from Not configured to Disabled.
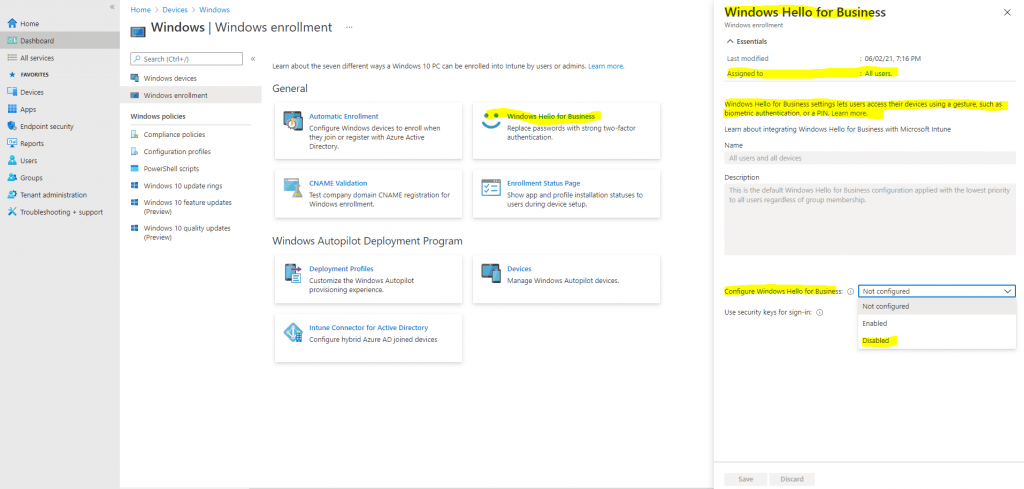
Enabled. Select this setting if you want to configure Windows Hello for Business settings. When you select Enabled, additional settings for Windows Hello are visible and can be configured for devices.
Disabled. If you don’t want to enable Windows Hello for Business during device enrollment, select this option. When disabled, users can’t provision Windows Hello for Business. When set to Disabled, you can still configure the subsequent settings for Windows Hello for Business even though this policy won’t enable Windows Hello for Business.
Not configured. Select this setting if you don’t want to use Intune to control Windows Hello for Business settings. Any existing Windows Hello for Business settings on Windows 10 devices isn’t changed. All other settings on the pane are unavailable.
Source: https://docs.microsoft.com/en-us/mem/intune/protect/windows-hello
After changing from Not configured to Disabled, a bunch of detailed settings for Windows Hello appeared you can still configure for Windows Hello for Business even though this policy won’t enable Windows Hello for Business.
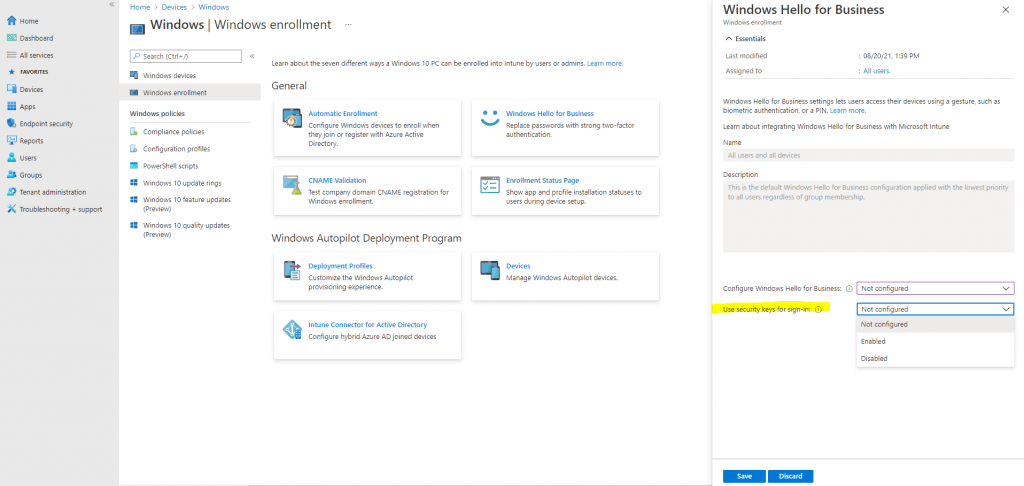
You can also configure here to use security keys for sign-in.
A security key is a physical device that you can use instead of your user name and password to sign in. It may be a USB key that you could keep on your keychain, or an NFC device like a smartphone or access card. Since it’s used in addition to a fingerprint or PIN, even if someone has your security key, they won’t be able to sign in without your PIN or fingerprint.
Source: https://support.microsoft.com/en-us/windows/sign-in-to-your-microsoft-account-with-windows-hello-or-a-security-key-800a8c01-6b61-49f5-0660-c2159bea4d84
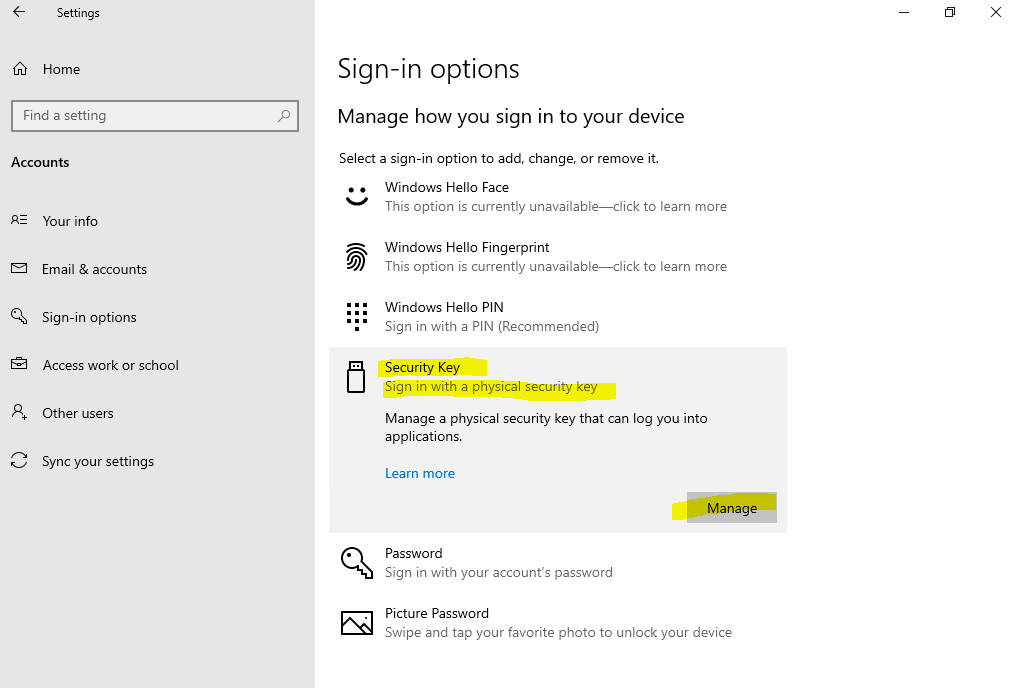
On the device you can manage the setting under Settings -> Accounts -> Sign-in options
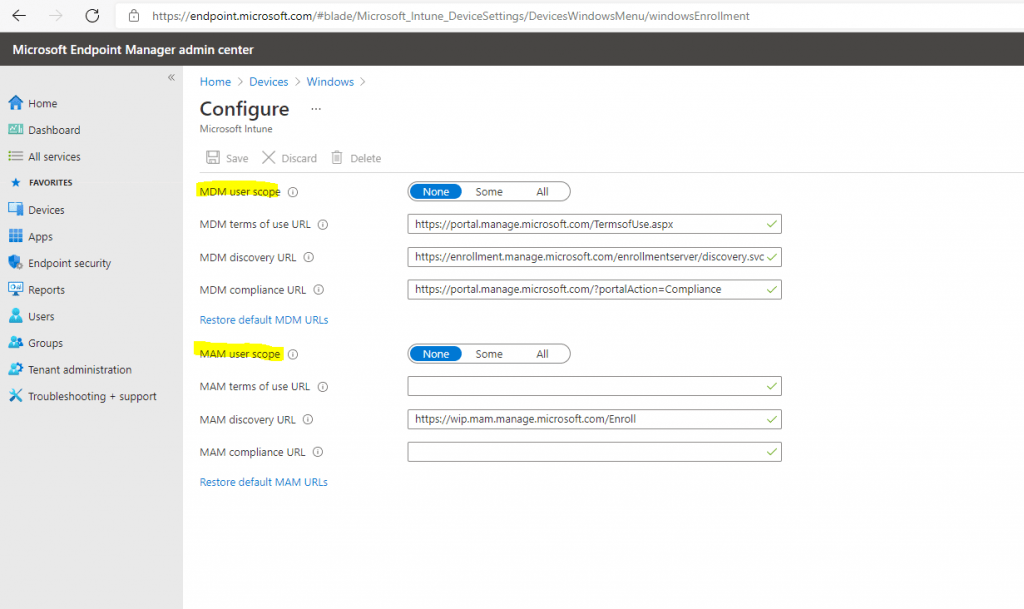
One further note about Microsoft Intune, which is a mobile device management (MDM) and mobile application management (MAM) provider.
If you want to join a device to Azure AD, where MDM Auto Enrollment is enabled at your tenant, the user who wants to join the device, needs a valid license for Microsoft Intune which is as mentioned for example included in the Enterprise Mobility + Security license.
Alternatively you can disable MDM Auto Enrollment by switching the following to None for all users or Some to use it only for users with a valid license.
For devices you want to disable Windows Hello, you need to enable MDM Auto Enrollment for the user who is joining the device to Azure AD.
Microsoft Endpoint Manager admin center under Devices -> Windows -> Windows enrollment
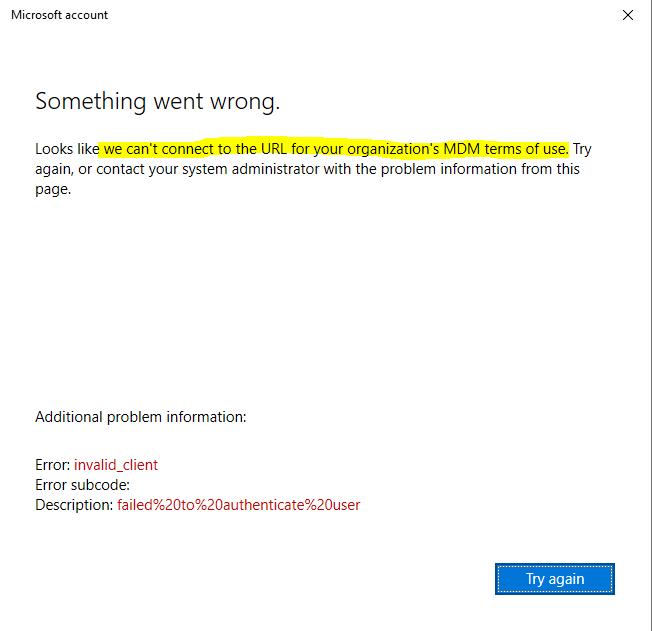
If MDM Auto Enrollment is enabled for the user who wants to join the device to Azure AD, and the user doesn’t have a valid license for Microsoft Intune, the user will run into the following error at trying to connect the device to Azure AD and after entering his credentials.
Something went wrong.
Looks like we can’t connect to the URL for your organization’s MDM terms of use. Try again, or contact your system administrator with the problem information from this page.
Windows Hello vs. Windows Hello for Business
In a nutshell, Windows Hello enables user’s to create a PIN or biometric gesture on their personal devices for convenient sign-in and is primarily used by consumers for standalone devices not domain joined.
Besides the convenient-sign-in it is also used to reduce the risk of keyloggers and phishing attacks, but the login process still uses the password hash in the background.
This configuration is referred to as Windows Hello convenience PIN and it is not backed by asymmetric (public/private key) or certificate-based authentication.
Windows Hello for Business in contrast is for businesses and enterprises that uses Active Directory and or Azure Active Directory and wants to implement a passwordless solution, it supports on-premises and hybrid deployments.
Windows Hello for Business is configured by Group Policy or mobile device management (MDM) policy and always uses key-based or certificate-based authentication. This makes it much more secure than Windows Hello convenience PIN.
When the identity provider supports keys, the Windows Hello for Business provisioning process creates a cryptographic key pair bound to the Trusted Platform Module (TPM), if a device has a TPM 2.0, or in software. Access to these keys and obtaining a signature to validate user possession of the private key is enabled only by the PIN or biometric gesture.
The two-step verification that takes place during Windows Hello for Business enrollment creates a trusted relationship between the identity provider and the user when the public portion of the public/private key pair is sent to an identity provider and associated with a user account. When a user enters the gesture on the device, the identity provider knows from the combination of Hello keys and gesture that this is a verified identity and provides an authentication token that allows Windows 10 to access resources and services.
The authenticating server has a public key that is mapped to the user account during the registration process. PIN entry and biometric gesture both trigger Windows 10 to use the private key to cryptographically sign data that is sent to the identity provider. The identity provider verifies the user’s identity and authenticates the user.
So in Windows Hello for Business neither the PIN nor the private portion of the credential are ever sent to the identity provider, except during provisioning.
Windows Hello as a convenience sign-in uses regular user name and password authentication, without the user entering the password.
Can I use a convenience PIN with Azure Active Directory?
It’s currently possible to set a convenience PIN on Azure Active Directory Joined or Hybrid Active Directory Joined devices. Convenience PIN is not supported for Azure Active Directory user accounts (synchronized identities included). It’s only supported for on-premises Domain Joined users and local account users.
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-faq#can-i-use-a-convenience-pin-with-azure-active-directory
Microsoft is committed to its vision of a world without passwords. We recognize the convenience provided by convenience PIN, but it stills uses a password for authentication. Microsoft recommends that customers using Windows 10 and convenience PINs should move to Windows Hello for Business. New Windows 10 deployments should deploy Windows Hello for Business and not convenience PINs.
Microsoft will be deprecating convenience PINs in the future and will publish the date early to ensure customers have adequate lead time to deploy Windows Hello for Business.
Source: https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-faq#what-about-convenience-pin
More technical details about how Windows Hello for Business works you will find in the following Microsoft articles.
Windows Hello for Business Overview
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview#how-windows-hello-for-business-works-key-points
Why a PIN is better than a password
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-why-pin-is-better-than-password
How Windows Hello for Business works
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-how-it-works
Manage Windows Hello for Business in your organization
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization
About how to set up Windows Hello for Business, you can also read my following post.
Determine if Windows Hello for Business is used for your Windows Sign In
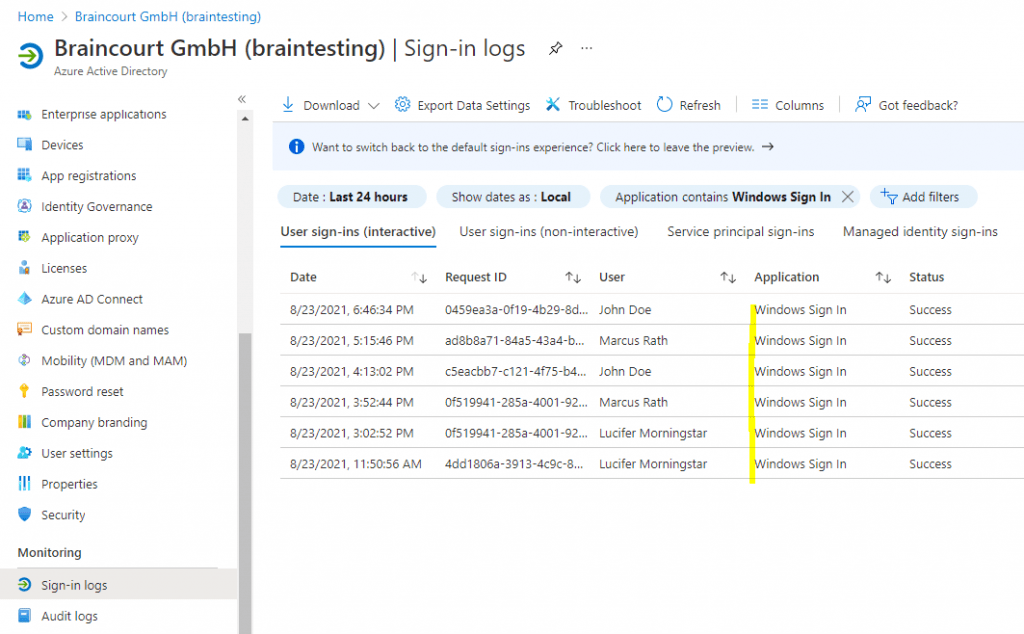
To finally check if Windows Hello for Business is used for the Windows Sign In on a Azure AD joined device, you can check the Sign-in logs from Azure AD as follows.
Azure Active Directory -> Sign-in logs
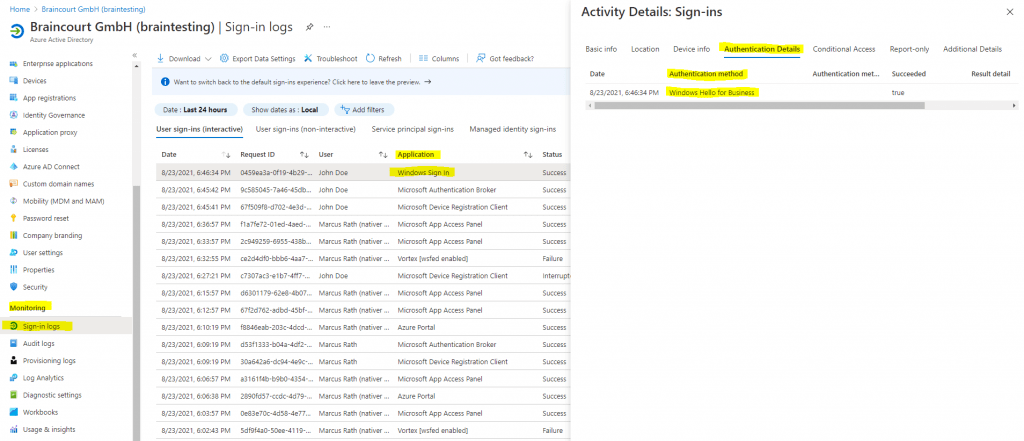
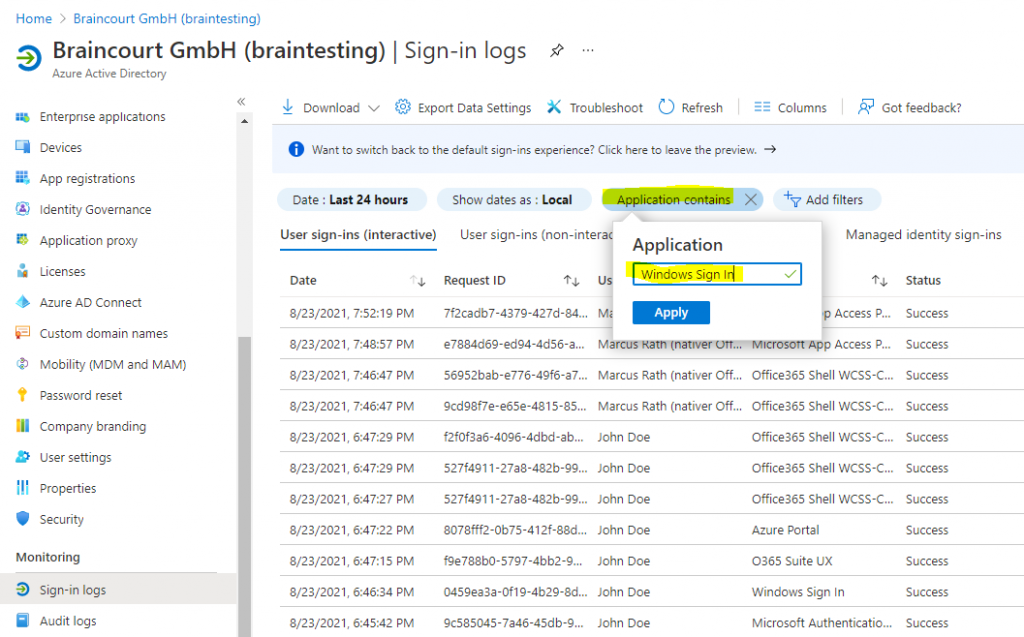
You can also add a filter to limit the logs only on Windows Sign In events as follows.
Click on Add filters
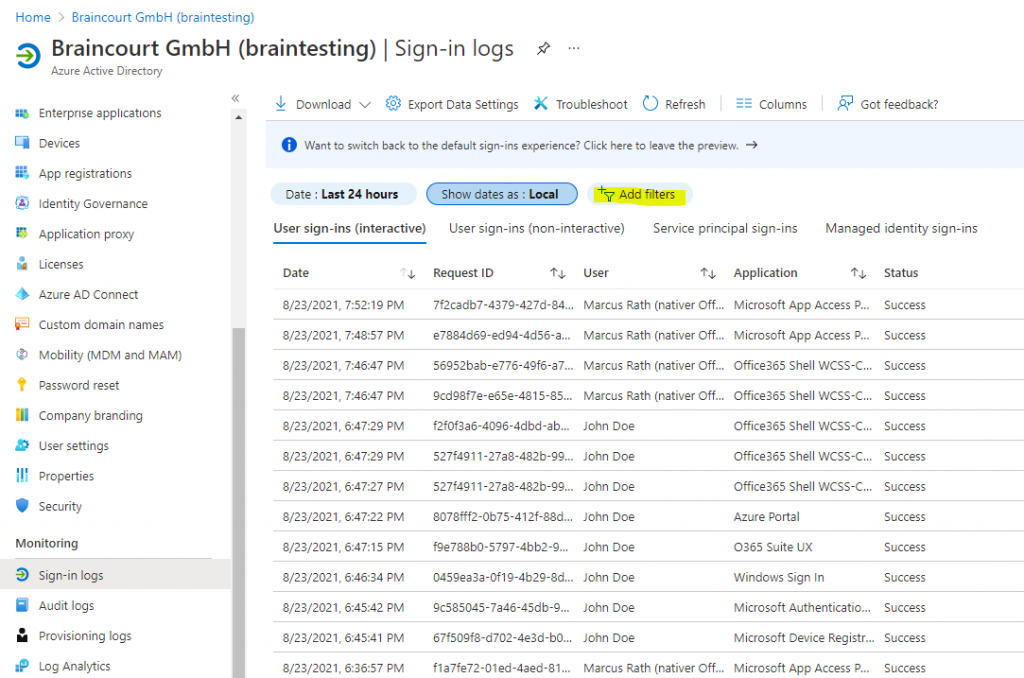
Select Application and click on Apply.
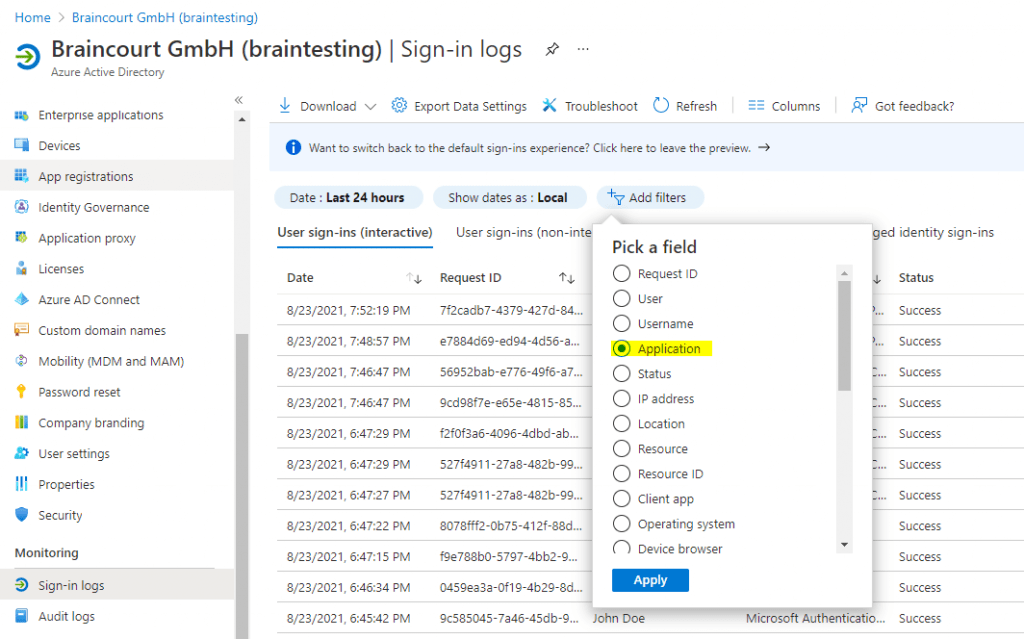
Add the name of the application in our case Windows Sign In and click on Apply.
Links
Windows Hello for Business documentation
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/
Microsoft Endpoint Manager overview
https://docs.microsoft.com/en-us/mem/endpoint-manager-overview
Sign in to your Microsoft account with Windows Hello or a security key
https://support.microsoft.com/en-us/windows/sign-in-to-your-microsoft-account-with-windows-hello-or-a-security-key-800a8c01-6b61-49f5-0660-c2159bea4d84
Why a PIN is better than a password
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-why-pin-is-better-than-password
Windows Hello for Business Overview
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-overview#benefits-of-windows-hello
How Windows Hello for Business works
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-how-it-works
Windows Hello for Business Frequently Asked Questions (FAQ)
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-faq
Integrate Windows Hello for Business with Microsoft Intune
https://docs.microsoft.com/en-us/mem/intune/protect/windows-hello
Manage Windows Hello for Business in your organization
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization
Hybrid Azure AD joined Key trust Windows Hello for Business Prerequisites
https://docs.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-hybrid-key-trust-prereqs



