PetitPotam NTLM Relay Attack – Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)
On actual occasion, I want to share some information about the newly uncovered security flaw in Windows operating systems named PetitPotam, which is based on NTLM Relay Attacks, and how you can prevent successful attacks.
Below you will find an Microsoft article to determine if your environment is potentially vulnerable to this attack and how you can mitigate the surface and risk for.
Microsoft is aware of PetitPotam which can potentially be used in an attack on Windows domain controllers or other Windows servers. PetitPotam is a classic NTLM Relay Attack, and such attacks have been previously documented by Microsoft along with numerous mitigation options to protect customers. For example: Microsoft Security Advisory 974926.
To prevent NTLM Relay Attacks on networks with NTLM enabled, domain administrators must ensure that services that permit NTLM authentication make use of protections such as Extended Protection for Authentication (EPA) or signing features such as SMB signing. PetitPotam takes advantage of servers where the Active Directory Certificate Services (AD CS) is not configured with protections for NTLM Relay Attacks. The mitigations below outline to customers how to protect their AD CS servers from such attacks.
You are potentially vulnerable to this attack if NTLM authentication is enabled in your domain and you are using Active Directory Certificate Services (AD CS) with any of the following services:
Certificate Authority Web Enrollment
Certificate Enrollment Web Service
Source: https://support.microsoft.com/en-us/topic/kb5005413-mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-3612b773-4043-4aa9-b23d-b87910cd3429
Mitigation
If your environment is vulnerable to this attack, we recommend one of the following mitigations:
Preferred mitigation: we recommend you disable NTLM authentication on your Windows domain controller as the simplest mitigation. This can be accomplished by following the documentation in Network security: Restrict NTLM: NTLM authentication in this domain.
Other Mitigations: If you are unable to disable NTLM on your domain for compatibility reasons, you can do one of the following. They are listed in order of more secure to less secure:
- Disable NTLM on any AD CS Servers in your domain using the group policy Network security: Restrict NTLM: Incoming NTLM traffic. To configure this GPO, open Group Policy and go to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options and set “Network security: Restrict NTLM: Incoming NTLM traffic” to “Deny All Accounts” or “Deny All domain accounts”. If needed you can add exceptions as necessary using the setting “Network security: Restrict NTLM: Add server exceptions in this domain.”
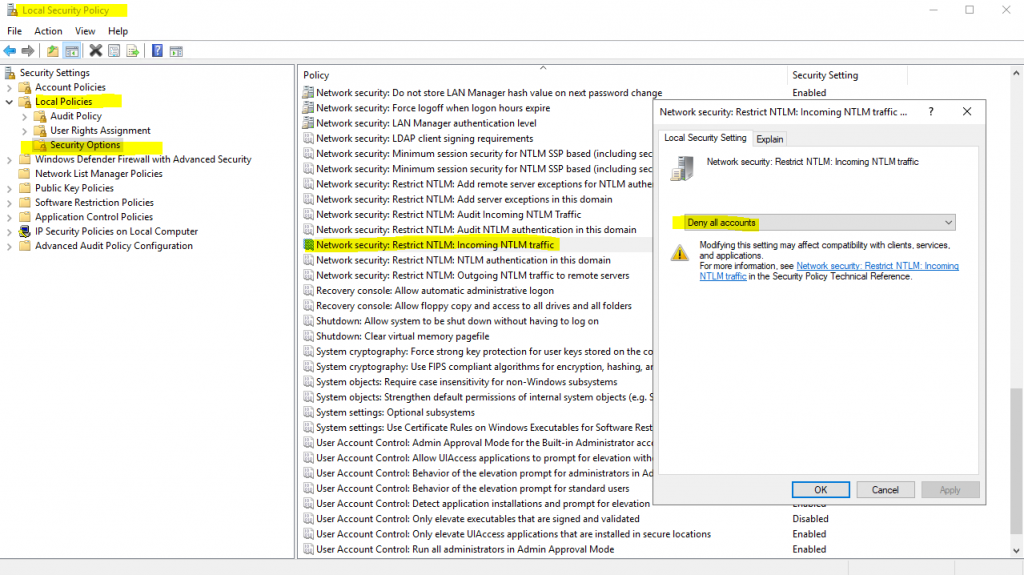
- Disable NTLM for Internet Information Services (IIS) on AD CS Servers in your domain running the “Certificate Authority Web Enrollment” or “Certificate Enrollment Web Service” services.
To do so open IIS Manager UI, set Windows authentication to “Negotiate:Kerberos”:
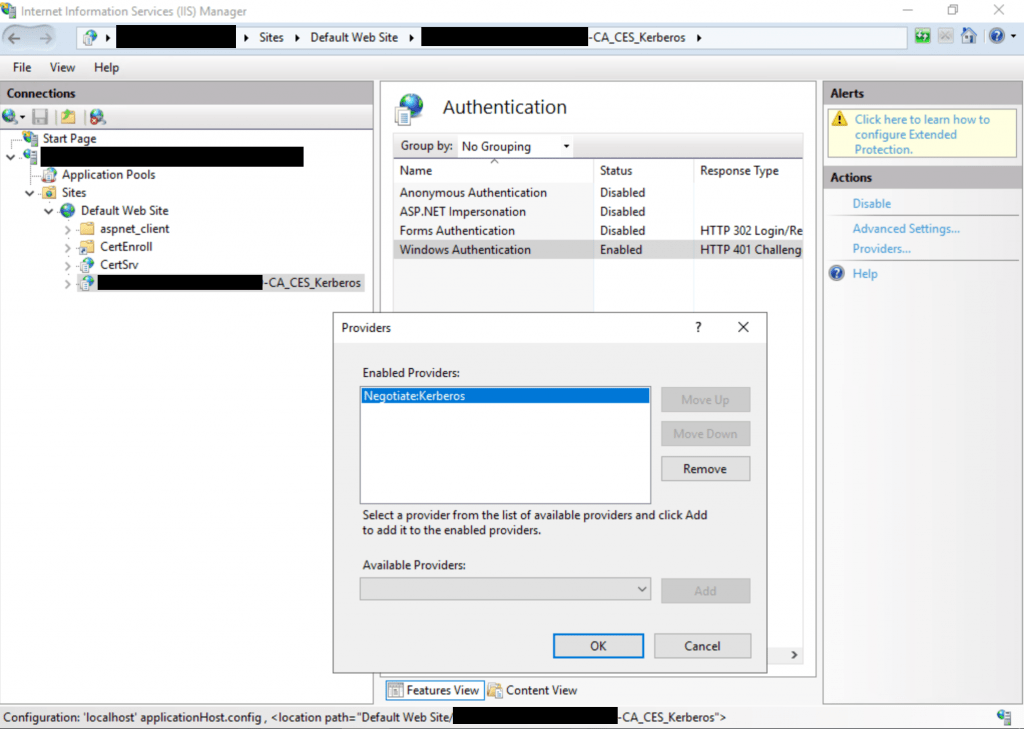
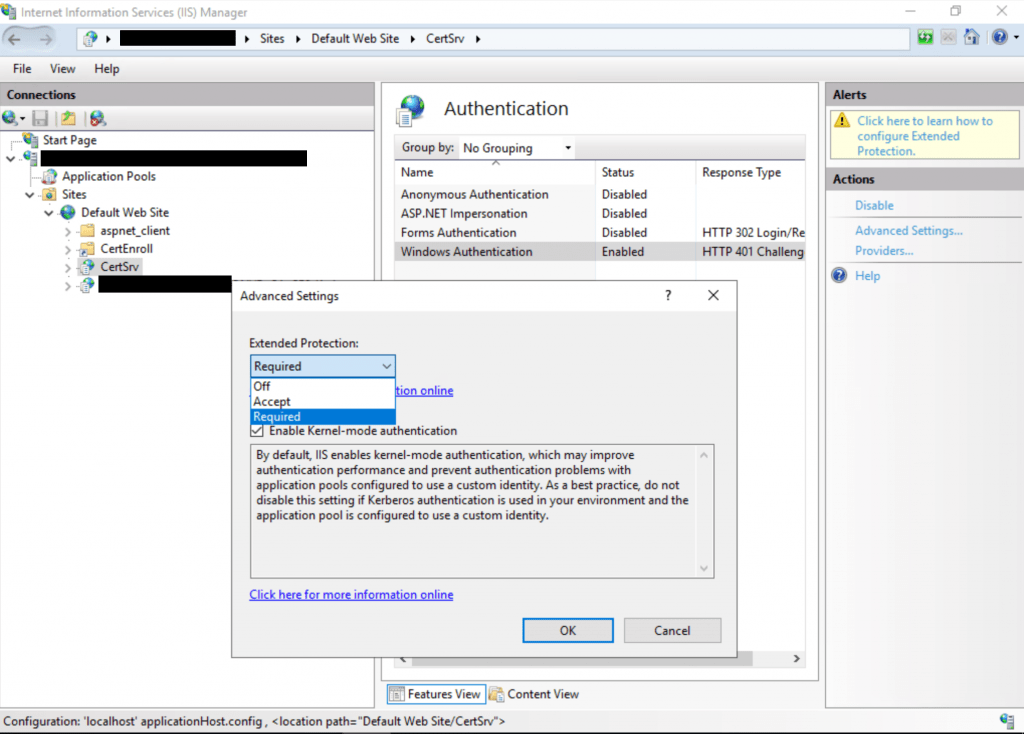
However, if you can’t disable NTLM outright then we recommend enabling EPA on AD CS services. This is achieved by:
Certificate Authority Web Enrollment
Links
New PetitPotam NTLM Relay Attack Lets Hackers Take Over Windows Domains
https://thehackernews.com/2021/07/new-petitpotam-ntlm-relay-attack-lets.html
KB5005413: Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS)
https://support.microsoft.com/en-us/topic/kb5005413-mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-3612b773-4043-4aa9-b23d-b87910cd3429
Mitigating NTLM Relay Attacks on Active Directory Certificate Services (AD CS) – ADV210003 – KB5005413 – PetitPotam
https://blog.truesec.com/2021/07/25/mitigating-ntlm-relay-attacks-on-active-directory-certificate-services-ad-cs-adv210003-kb5005413-petitpotam/
Windows-Netze verwundbar für Relay-Angriff PetitPotam
https://www.heise.de/news/Windows-Netze-verwundbar-fuer-Relay-Angriff-PetitPotam-6147467.html



