Set up Active Directory Federation Services (AD FS 5.0) – Internal ADFS Server – Part 1
In this post we will see how to set up an AD FS environment with an AD FS server in the internal network and an AD FS Reverse Proxy provided by the Web Application Proxy (WAP) and Remote Access server role in the perimeter network.
What’s new in Active Directory Federation Services for Windows Server 2019
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/overview/whats-new-active-directory-federation-services-windows-server#whats-new-in-active-directory-federation-services-for-windows-server-2019
This post is split into multiple parts
Part 1 … will cover the installation from the internal ADFS ServerPart 2 … will cover the installation from the ADFS Reverse Proxy Server in the perimeter network
Part 3 … will cover all about certificates for an ADFS environmentPart 4 … we will create an ASP.NET Web Application (.NET Framework -Web Forms) and configure it to be claim aware using WS-FED.
Part 5 … we will create an ASP.NET Core Web Application (MVCs) and configure it to be claim aware using WS-FED.
Part 6 … we will create an ASP.NET Web Application (.NET Framework – MVC) and configure it to be claim aware by using OAuth 2.0 and OpenID Connect.
Part 7 … we will create an ASP.NET Core Web Application (MVC) and configure it to be claim aware by using OAuth 2.0 and OpenID Connect.
Part 8 … will explain and list all identity protocols, AD FS supports.
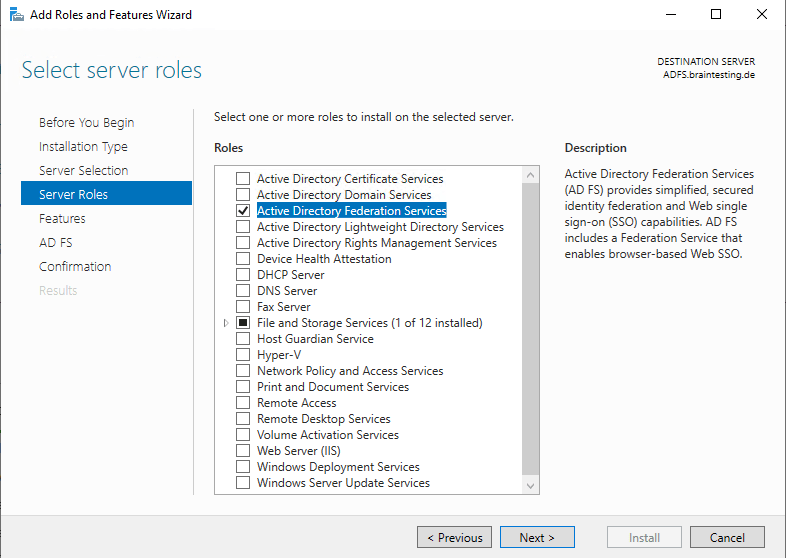
Installing the internal AD FS Server
You can install the AD FS server using the Server Manager and adding the server role Active Directory Federation Services or you can install it using PowerShell.
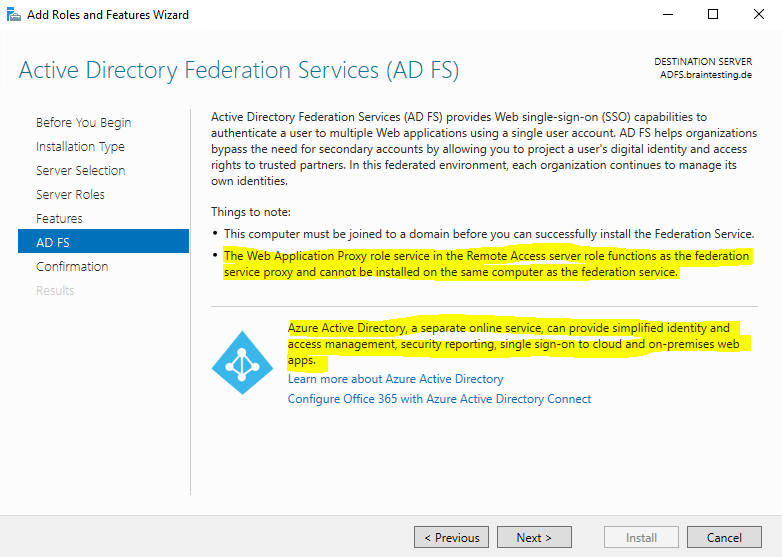
Here you will get the information that the ADFS-Reverse Proxy will be installed with the Web Application Proxy and Remote Access server role.
Further you will see that Azure AD will also provides you an Identity Provider (IdP) solution with SAML you can using instead of the ADFS server role at on-premises.
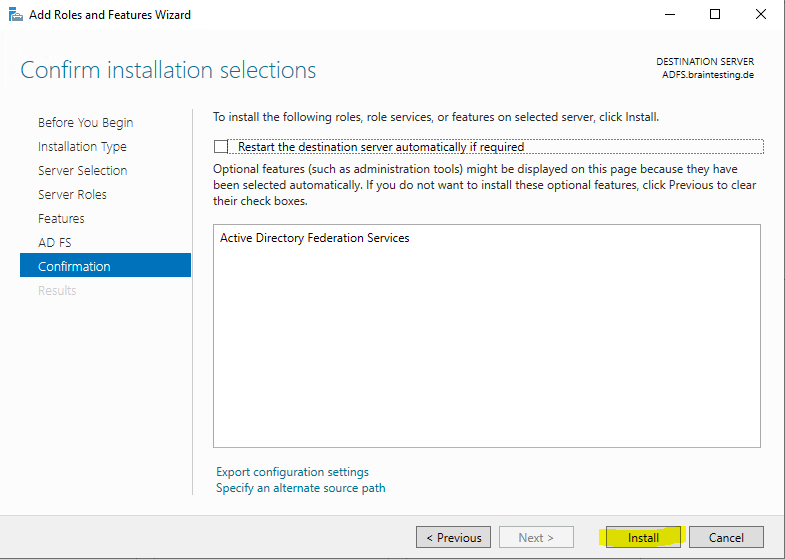
Here you can click directly on the link to configure ADFS or you can close the wizard and click on the warning icon within the server manager as shown below.
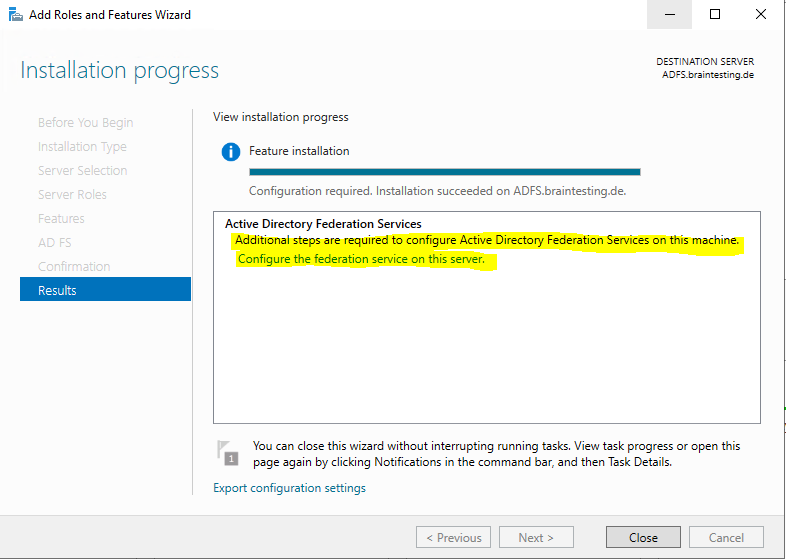
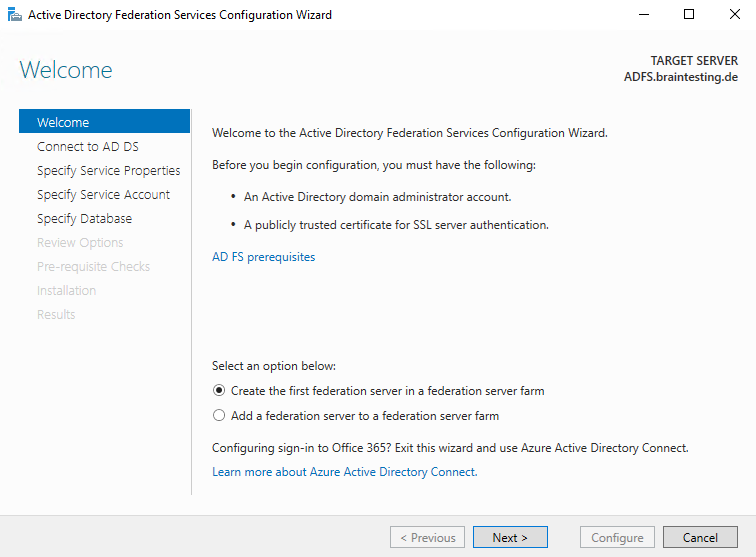
As this is the first federation server in my network I have to choose the following option.
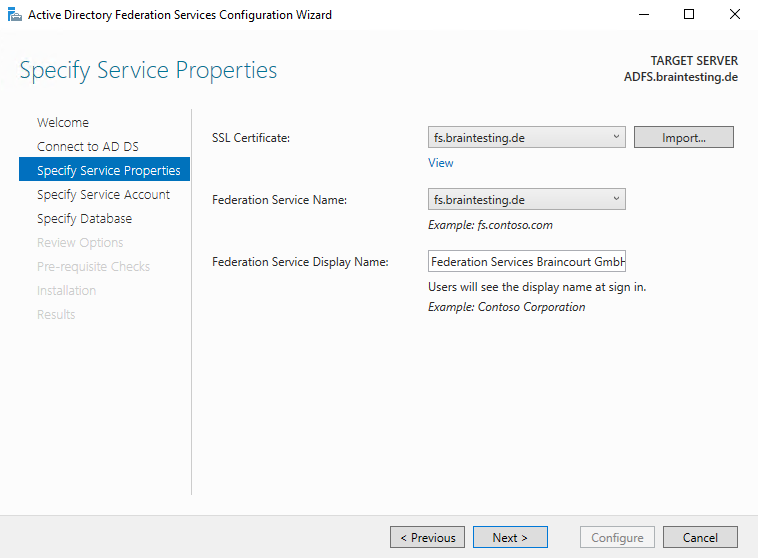
Select the Certificate which will be used as the SSL Certificate and the service communications certificate. In my case I will us a certificate from a trusted third party CA.
About the requirements about the certificates for an ADFS environment, you can read my following post.
The subject name and subject alternative name must contain your federation service name, such as fs.contoso.com.
So the federation service name is not by default the FQDN of the ADFS server itself and instead is derived from the certificate you choose here.
You also need to create a DNS A Record where you point the federation service name to the IP from the ADFS server. In my case I need to create a DNS A Record for fs.braintesting.de pointing to the ADFS.braintesting.de server.
Here you need to provide an user account which will run the ADFS Service. You can choose between an domain user account or Group Managed Service Account.
Regarding group Managed Service Account you can read more about in my following post.
I will create a new dedicated Group Managed Service Account.
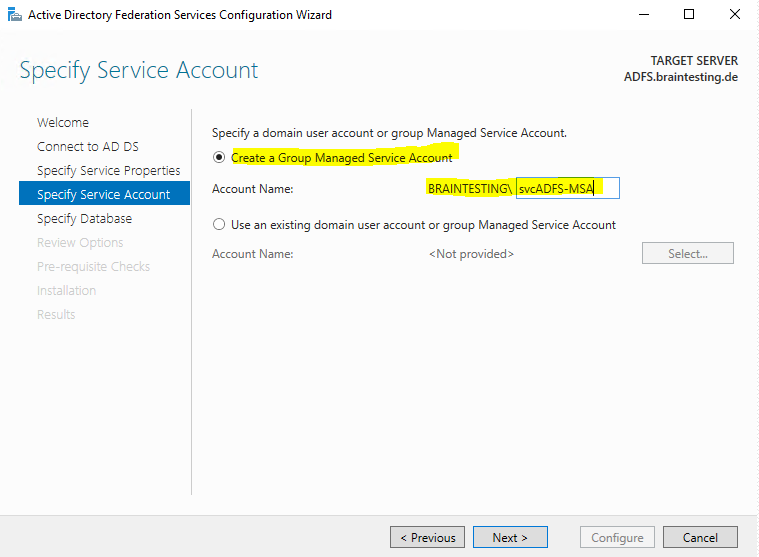
If you will run after clicking on Next into the following error:
Group Managed Service Accounts are not available because the KDS Root Key has not been set …
You have first to enable gMSA in your domainby running the follwing Windows PowerShell command on a domain controller, which runs Windows Server 2012 or later, in your Active Directory domain:
Add-KdsRootKey –EffectiveTime (Get-Date).AddHours(-10)
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/configure-a-federation-server#configure-the-first-federation-server-in-a-new-federation-server-farm
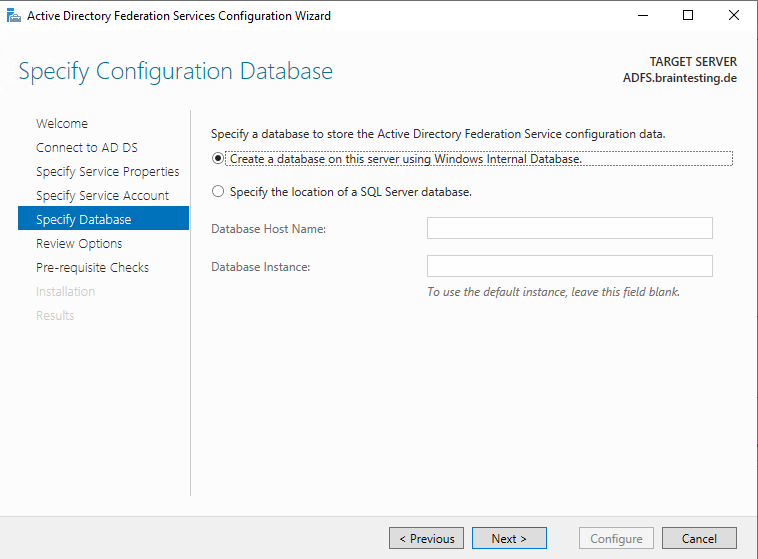
Here you can specify an already existing SQL Server in your network or using the Windows Internal Database which I will use.
Windows Internal Database (codenamed WYukon, sometimes referred to as SQL Server Embedded Edition)
https://en.wikipedia.org/wiki/Windows_Internal_Database
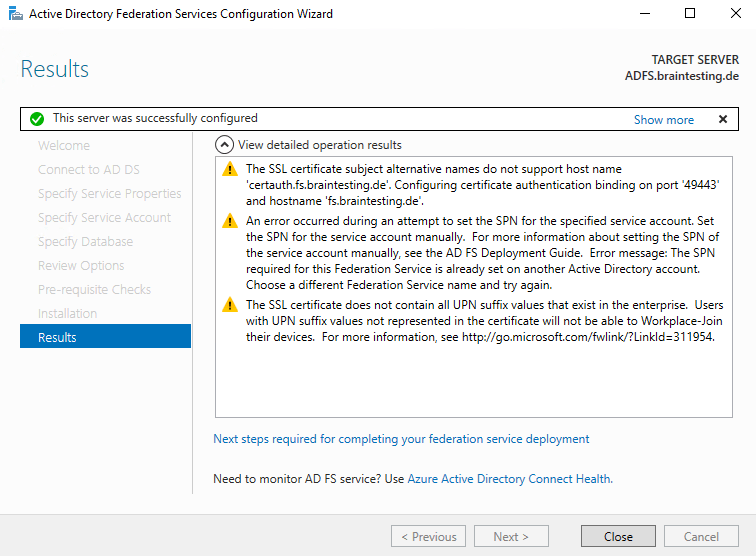
The following warnings we can ignore and belongs to certificate authentication.
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/operations/ad-fs-support-for-alternate-hostname-binding-for-certificate-authentication
The SSL certificate subject alternative names do not support host name ‘certauth.fs.braintesting.de’. Configuring certificate authentication binding on port ‘49443’ and hostname ‘fs.braintesting.de’.
An error occurred during an attempt to set the SPN for the specified service account. Set the SPN for the service account manually. For more information about setting the SPN of the service account manually, see the AD FS Deployment Guide. Error message: The SPN required for this Federation Service is already set on another Active Directory account. Choose a different Federation Service name and try again.
The SSL certificate does not contain all UPN suffix values that exist in the enterprise. Users with UPN suffix values not represented in the certificate will not be able to Workplace-Join their devices. For more information, see http://go.microsoft.com/fwlink/?LinkId=311954.
Enroll an SSL Certificate for AD FS
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/enroll-an-ssl-certificate-for-ad-fs
From now on we will have a new console to manage ADFS in the start menu.
Verify that a Federation Server is Operational
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/verify-that-a-federation-server-is-operational
You can use the following procedures to verify that a federation server is operational; that is, that any client on the same network can reach a new federation server.
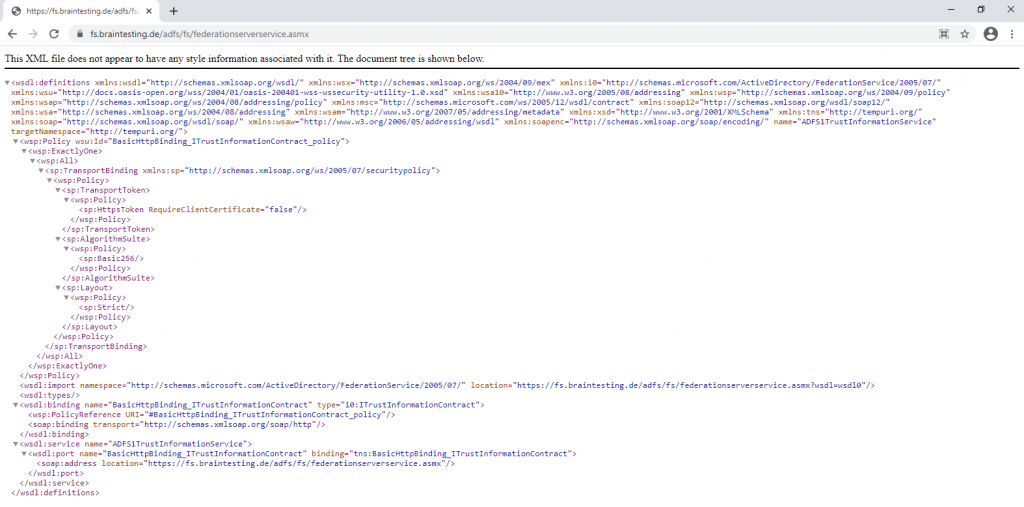
https://fs.braintesting.de/adfs/fs/federationserverservice.asmx
The expected output is a display of XML with the service description document. If this page appears, IIS on the federation server is operational and serving pages successfully.
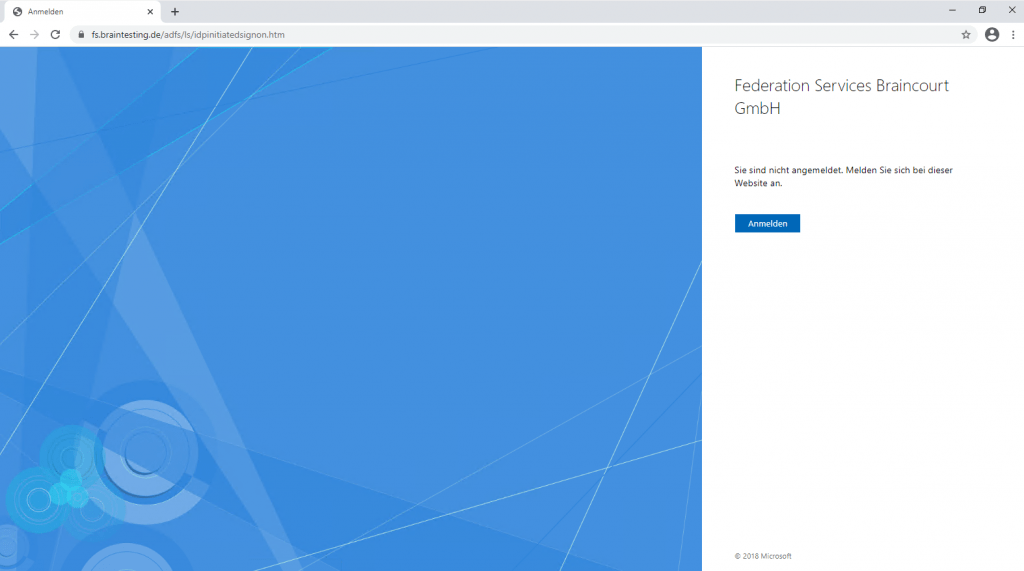
Also check if the AD FS sign-on page is enabled, by default it is disabled in Windows Server 2016 and 2019.
Verify the ADFS Sign-In Page
https://fs.braintesting.de/adfs/ls/idpinitiatedsignon.htm
AD FS Troubleshooting – Idp-Initiated Sign On
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-initiatedsignon
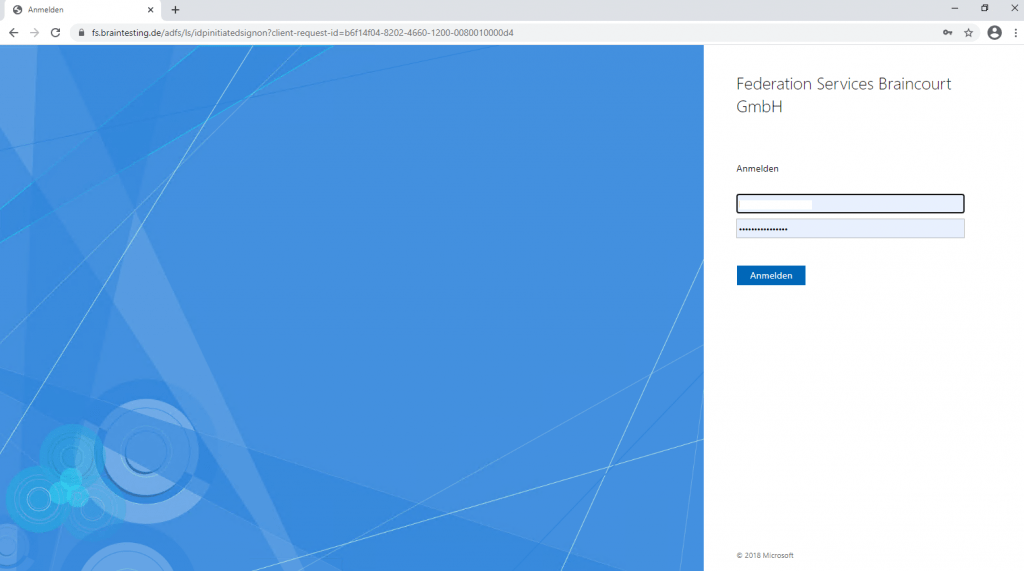
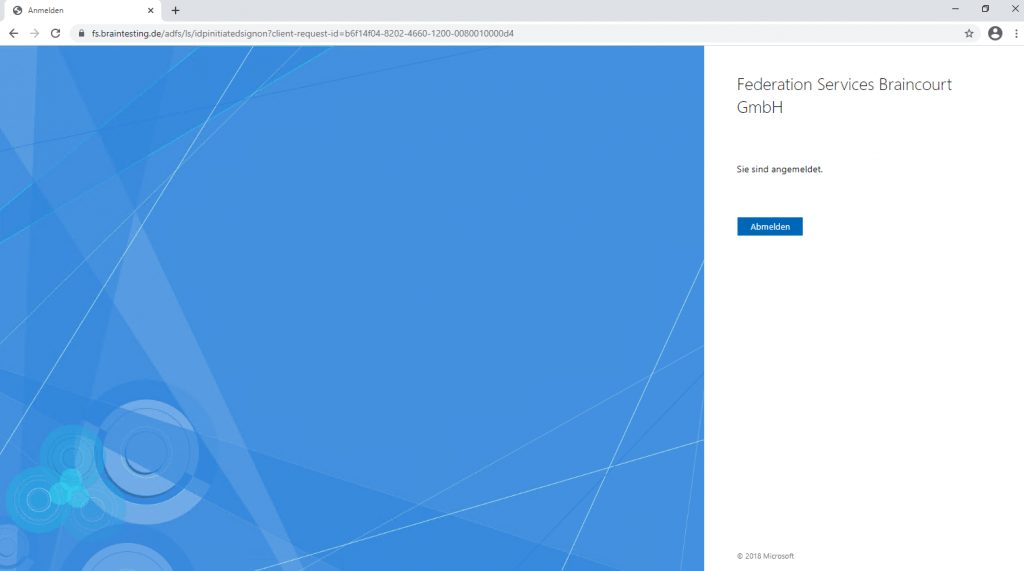
The AD FS sign-on page can be used to test whether or not authentication is working. This is done by navigating to the page and signing in. Also, we can use the sign-in page to verify that all SAML 2.0 relying parties are listed.
Enable the Idp-Initiated Sign on page
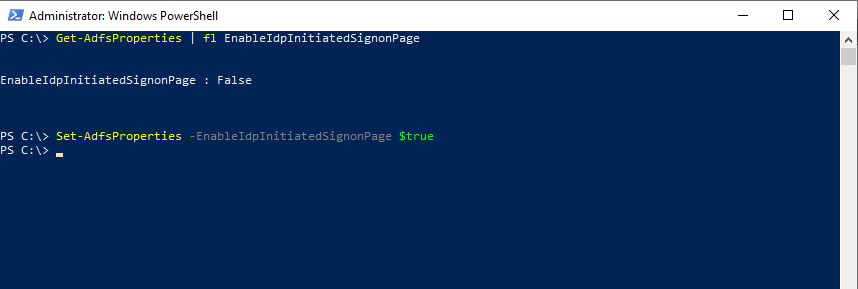
By default, AD FS in Windows 2016 does not have the sign on page enabled. In order to enable it you can use the PowerShell command Set-AdfsProperties. Use the following procedure to enable the page:
Get-AdfsProperties | fl EnableIdpInitiatedSignonPage
Set-AdfsProperties -EnableIdpInitiatedSignonPage $true
Troubleshooting AD FS
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/troubleshooting/ad-fs-tshoot-overview
Installing ADFS with PowerShell
AD FS
https://docs.microsoft.com/en-us/powershell/module/adfs/?view=windowsserver2019-ps
This reference provides command-line reference documentation for the IT professional of the Windows PowerShell cmdlets that you can use to deploy and administer Active Directory Federation Services (AD FS) in Windows Server.
Using PowerShell Cmdlets
Install-AdfsFarm
https://docs.microsoft.com/en-us/powershell/module/adfs/install-adfsfarm
Remove ADFS
Remove ADFS-Proxy
Remove-WindowsFeature Web-Application-Proxy,CMAK,RSAT-RemoteAccess
Remove internal ADFS Role
Remove-WindowsFeature ADFS-Federation,Windows-Internal-Database
Remove-WindowsFeature ADFS-Federation,Windows-Internal-Database
Links
AD FS Overview
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/ad-fs-overview
AD FS Help
https://adfshelp.microsoft.com/
SAML Tokens and Claims
https://docs.microsoft.com/en-us/dotnet/framework/wcf/feature-details/saml-tokens-and-claims
What Is SAML, and Why Does It Exist?
https://duo.com/blog/the-beer-drinkers-guide-to-saml
Kurz erklärt: SAML für sichere, komfortable Webzugänge
https://www.univention.de/blog-de/2019/06/saml-fuer-sichere-komfortable-webzugaenge-kurz-erklaert/
Security token service (STS)
https://en.wikipedia.org/wiki/Security_token_service
In Part 2 we will see how to set up the AD FS Proxy server in the perimeter network to publish the internal ADFS server to the internet.



